Category: HelpnetSecurity
There will be no patches for EOL Zyxel routers under attack via CVE-2024-40891, the company has confirmed. Meanwhile, Netgear has…
Satori announced its new capabilities, enabling security teams to be in control of all customer data across the development lifecycle…
Veriti launched Veriti Cloud, an expansion of its Exposure Assessment and Remediation platform that brings proactive cloud native remediation to…
A number of iOS and Android apps on Apple’s and Google’s official app stores contain a software development kit (SDK)…
Dynatrace announced the expansion of its security portfolio with a new Cloud Security Posture Management (CSPM) solution. For enterprises managing…
OpenNHP is the open-source implementation of NHP (Network-resource Hiding Protocol), a cryptography-based zero trust protocol for safeguarding servers and data….
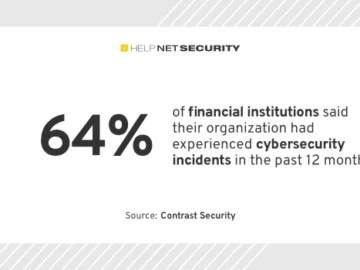
Financial institutions will continue to be the ultimate targets for criminals and threat actors, as a successful attack offers a…
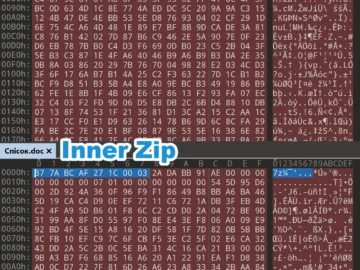
CVE-2025-0411, a Mark-of-the-Web bypass vulnerability in the open-source archiver tool 7-Zip that was fixed in November 2024, has been exploited…
Nymi launched next-generation wearable authenticator, the Nymi Band 4, which introduces design upgrades and expanded passwordless use cases for regulated…
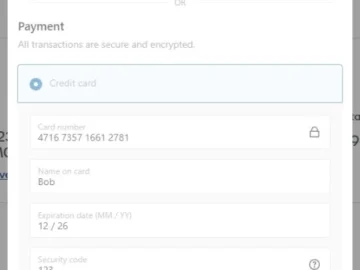
Japanese electronics maker Casio has had its UK website injected with a web skimmer that collected buyers’ personal and payment…
Join cybersecurity expert Jonathan Mayled from 5-hour Energy as he uncovers the limitations of log-based SIEMs and the transformative role…
Application Security Architect ReversingLabs | Ireland | Remote – View job details As an Application Security Architect, you will conduct…