Category: HelpnetSecurity
This list of ransomware-focused cybersecurity books is tailored for professionals seeking practical insights and deeper knowledge. Covering technical strategies, real-world…
CISO Sempra Infrastructure | USA | Hybrid – View job details As a CISO, you will develop and implement a…
We’ve entered a new era where verification must come before trust, and for good reason. Cyber threats are evolving rapidly,…
In this Help Net Security, Nicholas Jackson, Director of Cyber Operations at Bitdefender, discusses how technologies like AI, quantum computing,…
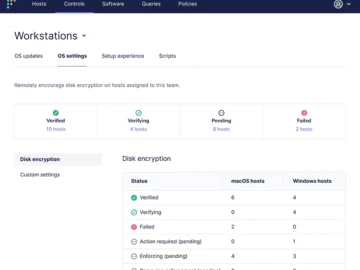
Fleet is an open-source platform for IT and security teams managing thousands of computers. It’s designed to work seamlessly with…
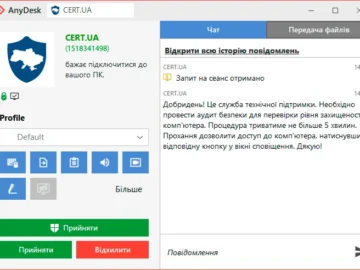
Attackers are impersonating the Computer Emergency Response Team of Ukraine (CERT-UA) via AnyDesk to gain access to target computers. The…
The twin cryptocurrency and digital identity revolutions are supposed to be building a better future, where anybody can take charge…
In this Help Net Security interview, Arunava Bag, CTO at Digitate, discusses how organizations can recover digital operations after an…
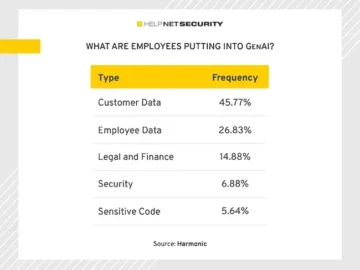
Despite their potential, many organizations hesitate to fully adopt GenAI tools due to concerns about sensitive data being inadvertently shared…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Attackers are encrypting AWS S3…
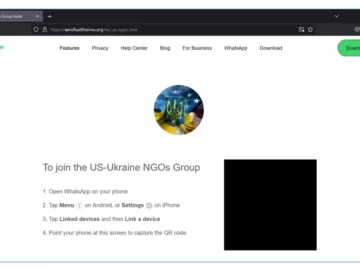
Star Blizzard, a threat actor tied to the Russian Federal Security Service (FSB), was spotted attempting to compromise targets’ WhatsApp…
In an exciting development for organizations struggling with data security, 1touch.io has announced its Sensitive Data Intelligence platform as a…