Category: HelpnetSecurity
Fragmented data from multiple scanners, siloed risk scoring and poor cross-team collaboration are leaving organizations increasingly exposed to breaches, compliance…
Six vulnerabilities have been fixed in the newest versions of Rsync (v3.4.0), two of which could be exploited by a…
In this Help Net Security interview, Mel Morris, CEO of Corpora.ai, discusses how cognitive biases affect decision-making during cybersecurity incidents….
Contextal Platform is an open-source cybersecurity solution for contextual threat detection and intelligence. Developed by the original authors of ClamAV,…
Cybersecurity is entering a new era of complexity, according to the World Economic Forum’s Global Cybersecurity Outlook 2025 report. Growing…
Microsoft has marked January 2025 Patch Tuesday with a hefty load of patches: 157 CVE-numbered security issues have been fixed…
Fortinet has patched an authentication bypass vulnerability (CVE-2024-55591) affecting its FortiOS firewalls and FortiProxy web gateways that’s being exploited by…
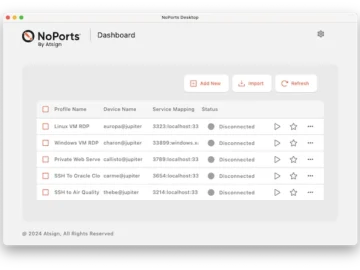
Atsign announced its new desktop client. This tool makes the protection of critical infrastructure easier by empowering people of all…
From zero-day exploits to weaknesses in widely used software and hardware, the vulnerabilities uncovered last year underscore threat actors’ tactics…
In 2025, CISOs will have powerful new capabilities as generative artificial intelligence (GenAI) continues to mature. Evolving beyond providing answers…
In this Help Net Security interview, Nuno Martins da Silveira Teodoro, VP of Group Cybersecurity at Solaris, discusses the latest…
Application Security Engineer ENOC | UAE | On-site – View job details As an Application Security Engineer, you will establish…