Category: HelpnetSecurity
Synology releases ActiveProtect, a new line of data protection appliances designed to provide enterprises a unified backup solution with simplicity,…
Wireshark, the popular network protocol analyzer, has reached version 4.4.3. Wireshark offers deep inspection across hundreds of protocols, live and…
Eliminating the inefficiencies, silos, unnecessary complexity, and coverage gaps that security practitioners have faced with fragmented security tools, the newly…
For decades, the CIS Critical Security Controls (CIS Controls) have simplified enterprises’ efforts to strengthen their cybersecurity posture by prescribing…
Sara is an open-source tool designed to analyze RouterOS configurations and identify security vulnerabilities on MikroTik hardware. Sara’s main feature…
In this Help Net Security interview, Josh Lemos, CISO at GitLab, talks about the shift from DevOps to DevSecOps, focusing…
As we look ahead to cybersecurity developments in 2025, there’s bad news and good—expect to see new challenging attacks and…
Ivanti has fixed two vulnerabilities affecting Ivanti Connect Secure, Policy Secure and ZTA gateways, one of which (CVE-2025-0282) has been…
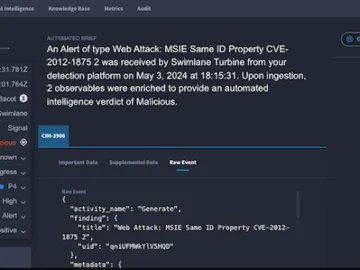
Swimlane unveiled Hero, a private agentic AI security operations (SecOps) companion. Built on the foundation of Swimlane’s Hero AI innovations,…
The White House has announced the launch of the U.S. Cyber Trust Mark, a voluntary cybersecurity labeling program for consumer-grade…
BioConnect introduced its Arc Series biometric devices. Designed to address the evolving security, compliance, and scalability needs of enterprises and…
CISA has added Mitel MiCollab (CVE-2024-41713, CVE-2024-55550) and Oracle WebLogic Server (CVE-2020-2883) vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog….