Category: HelpnetSecurity
Machine learning and generative AI are changing the way knowledge workers do their jobs. Every company is eager to be…
In this Help Net Security interview, Marko Simeonov, CEO of Plainsea, discusses how organizations can move beyond compliance-driven penetration testing…
Despite organizations’ repeated attempts at security awareness training, with a particular emphasis on how employees can avoid being phished, in…
AI Penetration Tester Microsoft | Canada | Remote – View job details As an AI Penetration Tester, you will discover…
The United Nation’s International Civil Aviation Organization (ICAO) confirmed on Monday that it’s “actively investigating reports of a potential information…
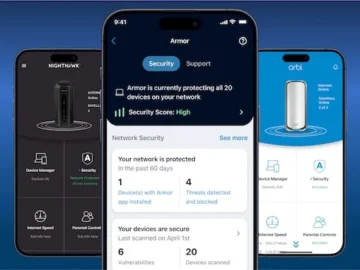
NETGEAR announced the next generation of NETGEAR Armor, powered by Bitdefender. As a subscription, Armor is a comprehensive cybersecurity service…
Enterprise cryptography faces risks beyond just the advent of quantum computers. For starters, there is no guarantee that the traditional…
In this Help Net Security interview, Sean Embry, CISO at eBay, discusses key aspects of cybersecurity leadership. He shares insights…
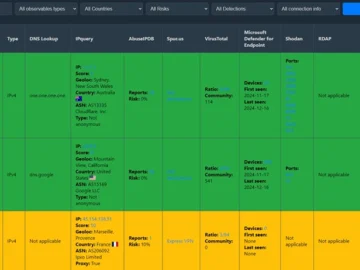
Cyberbro is an open-source application that extracts IoCs from garbage input and checks their reputation using multiple services. Cyberbro features…
This article presents key insights from 2024 reports on the rise of phishing attacks, focusing on how advancements in AI…
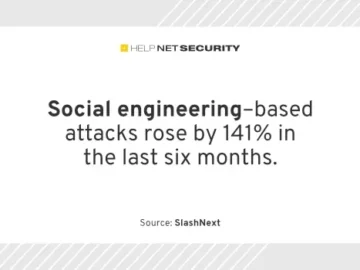
Phishing remains one of the most significant cyber threats impacting organizations worldwide, according to SlashNext. Credential phishing is raising Credential…
In this Help Net Security interview, Thomas Roccia, Senior Security Researcher at Microsoft, discusses how threat research drives faster, better…