Category: HelpnetSecurity
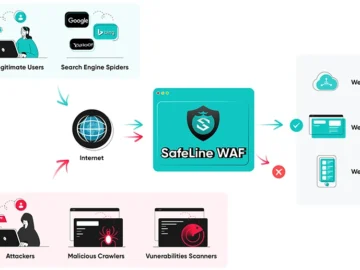
This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. SafeLine: Open-source…
Cybercriminals are using a variety of new methods to target organizations across industries. In this article, we examine the most…
In this Help Net Security interview, Vineet Chaku, President of Reaktr.ai, discusses how AI is transforming cybersecurity, particularly in anomaly…
reconFTW is an open-source tool that simplifies and automates the reconnaissance process, delivering subdomain enumeration, vulnerability assessment, and gathering intelligence…
86% of organizations had a security incident related to their cloud native environment within the last year, according to Venafi….
In this Help Net Security interview, Patrick Harding, Chief Architect at Ping Identity, discusses the growing threat of deepfake-related fraud…
In 2025, seven trends will shape the future of data and AI, offering advantages for those who see these changes…
A U.S. national survey of first responders reveals strong support for AI adoption, cybersecurity concerns, and increasing demand for cloud-native,…
Here’s a look at the most interesting products from the past month, featuring releases from: Appdome, Cato Networks, Datadog, Fortinet,…
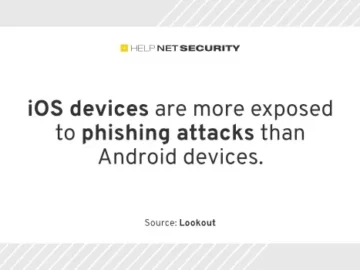
The mobile threat landscape continues to grow at an alarming rate as cybercrime groups shift their tactics and target mobile…
Service disruptions remain a critical concern for IT and business executives, with 88% of respondents saying they believe another major…
Managing cybersecurity and IT budgets is a critical element of organizational strategy. With increasing threats to data security, the rise…