Category: HelpnetSecurity
A 30-year old Romanian man was sentenced to 20 years in prison for leveraging the Netwalker ransomware to extort money…
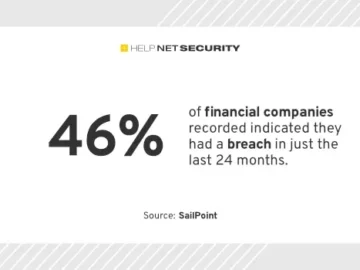
As the financial industry is the most targeted sector for data breaches in 2024, it’s now more important than ever…
In this Help Net Security interview, Anjos Nijk, Managing Director of the European Network for Cyber security (ENCS), discusses cybersecurity…
AI changes how organizations look at cybersecurityGenAI is compromising security while promising efficiency This article highlights key findings from 2024…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, GitGuardian, RunSafe Security, Stairwell,…
$2.2 billion worth of cryptocurrency was stolen from various platforms in 2024, Chainalysis’ 2025 Crypto Crime Report has revealed. Of…
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a binding operational directive (BOD 25-01) requiring federal civilian agencies…
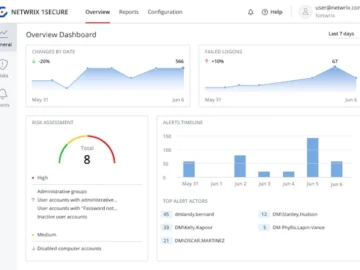
Netwrix released a new version of its SaaS platform, Netwrix 1Secure. The latest version builds on its existing security monitoring…
Ukrainian national Mark Sokolovsky was sentenced to 60 months in federal prison for one count of conspiracy to commit computer…
Security teams that subscribe to threat feeds get lists of known malicious domains, IPs, and file signatures that they can…
In this Help Net Security interview, Dan Lohrmann, CISO at Presidio, discusses the need for organizations to rethink their leadership…
In 2024, ransomware remained the top cybersecurity threat to organizations worldwide. New groups filled the void left by law enforcement…