Category: HelpnetSecurity
Security teams that subscribe to threat feeds get lists of known malicious domains, IPs, and file signatures that they can…
In this Help Net Security interview, Dan Lohrmann, CISO at Presidio, discusses the need for organizations to rethink their leadership…
In 2024, ransomware remained the top cybersecurity threat to organizations worldwide. New groups filled the void left by law enforcement…
A threat actor looking to take over the Microsoft Azure cloud infrastructure of European companies has successfully compromised accounts of…
BeyondTrust has fixed an unauthenticated command injection vulnerability (CVE-2024-12356) in its Privileged Remote Access (PRA) and Remote Support (RS) products…
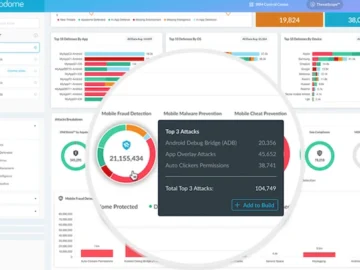
Appdome announced that the Appdome Mobile Defense Platform now protects applications running on mobile-enabled platforms like Apple macOS, Apple visionOS,…
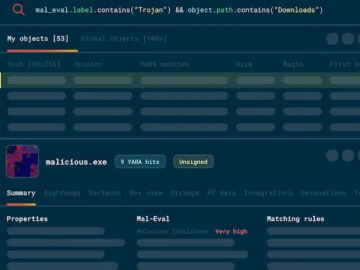
Stairwell announces Stairwell Core, which enables organizations to privately collect, store, and continuously reassess executable files so they can confidently…
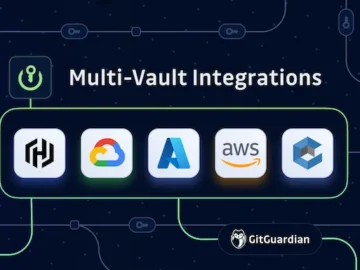
GitGuardian unveiled a comprehensive Non-Human Identity (NHI) security strategy with integrations across major secrets management platforms, addressing the growing challenge…
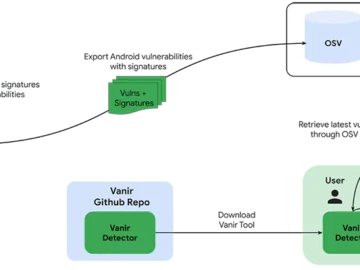
Google’s open-source tool Vanir enables Android developers to quickly scan custom platform code for missing or applicable security patches. By…
What was once primarily a technical role, CISOs now find themselves accountable for organizational risk, regulatory compliance, and even legal…
In this Help Net Security interview, Vivek Agarwal, Privacy Program Manager at Meta Platforms, shares insights on strategies for reducing…
Breaches in 2024 had less impact on consumers’ trust in brands compared to the previous year (a 6.5% decrease from…