Category: HelpnetSecurity
Cybersecurity has become one of the most high-stakes facets of business operations in the past few years. The chief information…
In this Help Net Security interview, Ben de Bont, CISO at ServiceNow, discusses AI governance, focusing on how to foster…
Keycloak is an open-source project for identity and access management (IAM). It provides user federation, strong authentication, user management, authorization,…
Since making Kerberos the default Windows authentication protocol in 2000, Microsoft has been working on eventually retiring NTLM, its less…
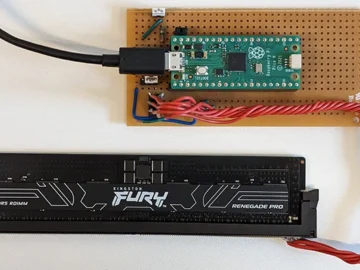
Cybersecurity researchers have identified a vulnerability (CVE-2024-21944, aka BadRAM) affecting ADM processors that can be triggered by rogue memory modules…
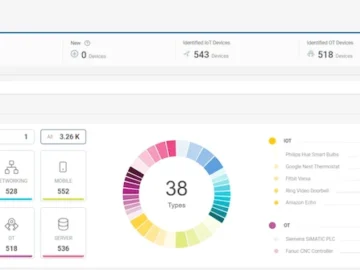
With the introduction of Cato IoT/OT Security, Cato Networks is enabling enterprises to simplify the management and security of Internet…
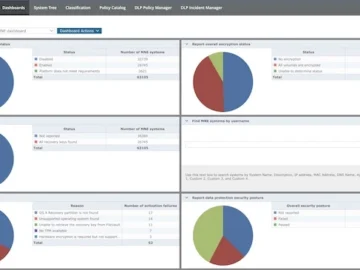
Trellix announced Trellix Drive Encryption upgrades for on-premises and SaaS management. Customers benefit from the flexibility needed for encryption protection…
Containers are the fastest growing – and weakest cybersecurity link – in software supply chains, according to NetRise. Companies are…
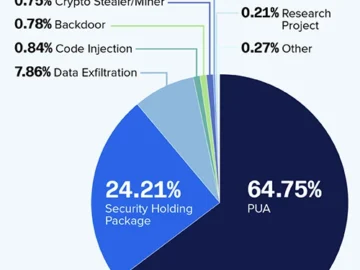
Sonatype’s 2024 Open Source Malware Threat Report reveals that the number of malicious packages has surpassed 778,500 since tracking began…
In this Help Net Security interview, Allison Ritter, Head of Cyber Experiential Exercising at Cyberbit, shares her insights on the…
On December 2024 Patch Tuesday, Microsoft resolved 71 vulnerabilities in a variety of its products, including a zero-day (CVE-2024-49138) that’s…
The Department of the Treasury is sanctioning Chinese cybersecurity company Sichuan Silence, and one of its employees, Guan Tianfeng, for…