Category: HelpnetSecurity
Researchers have published a proof-of-concept (PoC) exploit for CVE-2024-8785, a critical remote code execution vulnerability affecting Progress WhatsUp Gold, a…
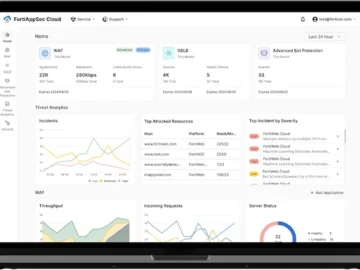
Fortinet announced FortiAppSec Cloud, a new cloud-delivered platform that integrates key web application security and performance management tools into a…
Veza announced Veza Access Requests product, enabling organizations to reduce the risk of identity-based threats with automated access policy intelligence…
High-risk access exists throughout the workplace, in almost every job role, proving that the time has come for organizations to…
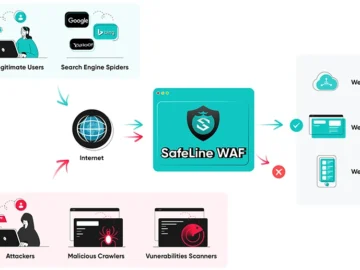
SafeLine is an open-source and self-hosted Web Application Firewall (WAF) that protects websites from cyber attacks. “SafeLine WAF was created…
In this Help Net Security interview, Niv Braun, CEO at Noma Security, discusses the difficulties security teams face due to…
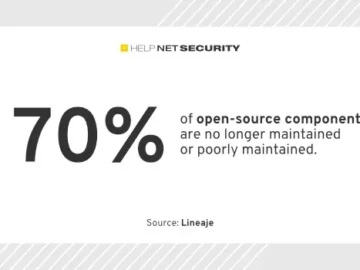
The geographic distribution of open-source contributions introduces geopolitical risks that organizations must urgently consider, especially with rising nation-state attacks, according…
Veeam has fixed two vulnerabilities in Veeam Service Provider Console (VSPC), one of which (CVE-2024-42448) may allow remote attackers to…
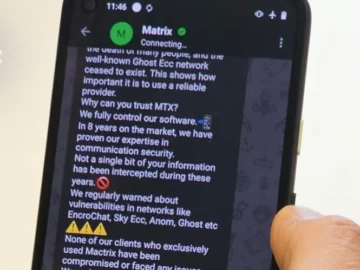
A joint investigation team involving French and Dutch authorities has taken down Matrix, yet another end-to-end encrypted chat service created…
The cyber world needs your expertise. But the security leaders of tomorrow require a broad set of skills that job…
Phishers have come up with a new trick for bypassing email security systems: corrupted MS Office documents. The spam campaign…
Sweet Security introduces unified Cloud Native Detection and Response platform, designed to transform the way organizations protect their cloud environments…