Category: HelpnetSecurity
ENGlobal, a Texas-based engineering and automation contractor for companies in the energy sector, has had its data encrypted by attackers….
Nextcloud has unveiled Nextcloud Talk, an open-source alternative to Microsoft Teams. It’s a privacy-compliant collaboration platform for hybrid teams that…
In this Help Net Security interview, Doug Kersten, CISO of Appfire, explains how treating AI like a human can change…
Application Security Engineer TE Connectivity | USA | Remote – View job details As an Application Security Engineer, you will…
Amazon Web Services (AWS) has launched a new service to help organizations prepare for and recover from ransomware attacks, account…
A coordinated international operation involving law enforcement agencies from 40 countries led to the arrest of over 5,500 individuals linked…
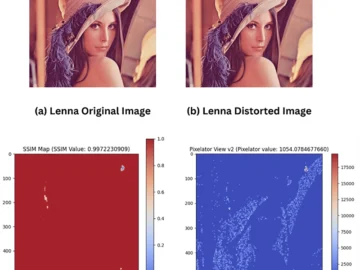
Pixelator v2 is a tool to spot fake images. It uses a new combination of image veracity techniques with capability…
In this Help Net Security interview, Alec Summers, Project Leader for the CVE Program at MITRE, shares his insights on…
Cybersecurity programs have evolved significantly over the past few decades. The advent of cloud computing shattered the conventional corporate perimeter,…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Researchers reveal exploitable flaws in…
In this Help Net Security interview, Steve Carter, CEO of Nucleus Security, discusses the ongoing challenges in vulnerability management, including…
Multiple regional conflicts, such as Russia’s continued invasion of Ukraine and the Israel-Hamas conflict, have resulted in a surge in…