Category: HelpnetSecurity
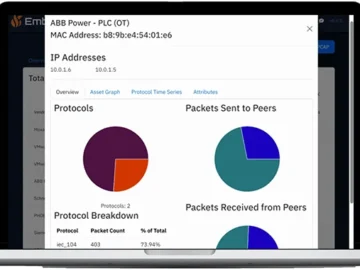
EmberOT’s OT PCAP Analyzer, developed for the industrial security community, is a free tool providing a high-level overview of the…
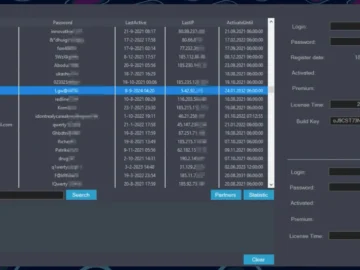
The Dutch National Police, along with partner law enforcement agencies, has disrupted the operation of the Redline and Meta infostealers…
Jumio unveiled Jumio Liveness, an enhanced, in-house technology designed to address increasingly sophisticated fraud tactics. This solution expands beyond traditional…
In the war against malicious cyber activity, it’s time for security vendors to step in – and it’s not how…
In this Help Net Security interview, Emily Long, CEO at Edera, discusses the most common vulnerabilities in Kubernetes clusters and…
Threat actors continue to probe the payments ecosystem for vulnerabilities and were successful in conducting fraud schemes affecting multiple financial…
The ethical and responsible use of technology is fast becoming part of the mandate for CIOs, as organizations balance the…
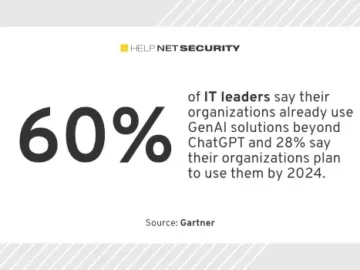
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Fortinet releases patches for publicly…
In this Help Net Security interview, Michael Daum, Head of Global Cyber Claims for Allianz Commercial, discusses the significant rise…
Climbing Mount Everest isn’t a feat for the faint hearted. Extreme weather, dangerous terrain and acclimatization requirements make the trek…
Due to widely varying government, risk, and compliance (GRC) tool pricing, enterprise risk management (ERM) leaders must understand four different…
Here’s a look at the most interesting products from the past week, featuring releases from Fastly, IBM, Ivanti, Kusari, and…