Category: HelpnetSecurity
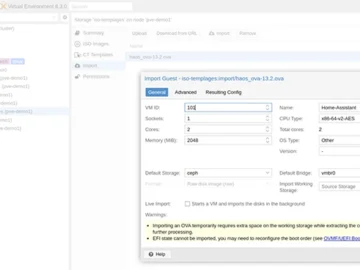
The Proxmox Virtual Environment 8.3 enterprise virtualization solution features management tools and a user-friendly web interface, allowing you to deploy…
In this Help Net Security interview, Ben Colman, CEO of Reality Defender, discusses the challenges of detecting high-quality deepfakes in…
As cybercriminals continue to adapt their techniques to find new ways through defenses, AI-assisted fraud is growing increasingly sophisticated and…
Ransomware gangs recruit pen testers to improve attack reliabilityThreat actors employ pen testers to improve ransomware effectiveness Threat actors are…
Here’s a look at the most interesting products from the past week, featuring releases from Aon, Arkose Labs, HiddenLayer, Hornetsecurity,…
Law enforcement unsealed criminal charges against five alleged members of Scattered Spider, who allegedly targeted employees of companies nationwide with…
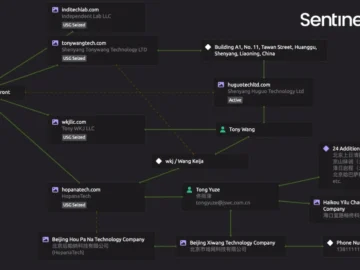
An analysis of the websites belonging to companies that served as a front for getting North Korean IT workers remote…
Attackers have compromised around 2,000 Palo Alto Networks firewalls by leveraging the two recently patched zero-days (CVE-2024-0012 and CVE-2024-9474), Shadowserver…
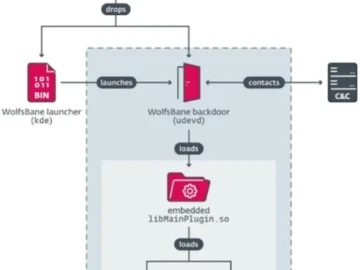
ESET researchers have identified multiple samples of two previously unknown Linux backdoors: WolfsBane and FireWood. The goal of the backdoors…
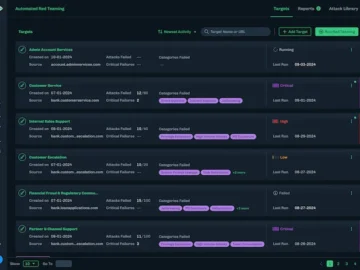
HiddenLayer launched Automated Red Teaming solution for artificial intelligence, a transformative tool that enables security teams to rapidly and thoroughly…
The Computer Emergency Response Team of Ukraine (CERT-UA), part of the State Service of Special Communications and Information Protection (SSSCIP),…
The CWE list of the 25 most dangerous software weaknesses demonstrates the currently most common and impactful software flaws. Identifying…