Category: HelpnetSecurity
Hijacking domains using a ‘Sitting Ducks attack’ remains an underrecognized topic in the cybersecurity community. Few threat researchers are familiar…
Cyber crooks are trying out an interesting new approach for getting information-stealing malware installed on Android users’ smartphones: a physical…
Attackers have been spotted exploiting two additional vulnerabilities (CVE-2024-9463, CVE-2024-9465) in Palo Alto Networks’ Expedition firewall configuration migration tool, CISA…
In this Help Net Security interview, Tony Perez, CEO at NOC.org, discusses the role of continuous monitoring for real-time threat…
Finance and insurance sectors found to have the highest number of critical vulnerabilities, according to Black Duck. Finance and insurance…
Here’s a look at the most interesting products from the past week, featuring releases from Absolute Security, BlackFog, Eurotech, Nirmata,…
NIST’s latest report, “Hardware Security Failure Scenarios: Potential Hardware Weaknesses” (NIST IR 8517), explores the hidden vulnerabilities in computer hardware,…
The National Institute of Standards and Technology (NIST) is clearing the backlog of unprocessed CVE-numbered vulnerabilities in the National Vulnerability…
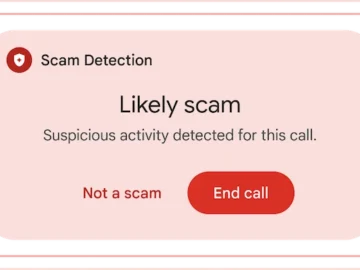
Google has announced new security features for Android that provide real-time protection against scams and harmful apps. These features, powered…
After months of news reports that Chinese threat actors have breached the networks of US telecommunications and internet service providers,…
CVE-2024-43451, a Windows zero-day vulnerability for which Microsoft released a fix on November 2024 Patch Tuesday, has been exploited since…
A joint report by leading cybersecurity agencies from the U.S., UK, Canada, Australia, and New Zealand has identified the most…