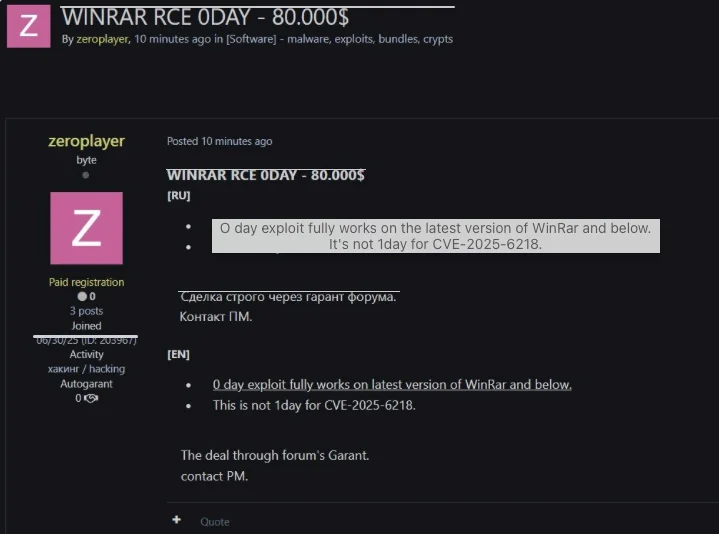
Category: HelpnetSecurity
State-sponsored hackers and financially motivated attackers continue leveraging a critical WinRAR vulnerability (CVE-2025-8088) that’s been fixed over half a year…
MIND announced DLP for Agentic AI, a data-centric approach to AI security designed to help organizations safely achieve the business…
France intends to phase out non-European videoconferencing platforms such as Zoom and Microsoft Teams from its public administration, opting instead…
Teams using automation platforms are starting to treat conversational AI as another operational interface. That change is reflected in a…
Teleport has unveiled the Teleport Agentic Identity Framework, an AI-centered framework that provides organizations with a roadmap for securely deploying…
To add an extra layer of protection to its end-to-end encryption, WhatsApp has begun rolling out a new privacy and…
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use….
Once a secret enters Git, it’s expensive to remediate. But the real problem runs deeper than cost. Grégory Maitrallain, Solution…
CERT UEFI Parser, a new open-source security analysis tool from the CERT Coordination Center has been released to help researchers…
A new study shows that some of the most widely used AI-powered browser extensions are a privacy risk. They collect…
Security and risk teams often rely on documentation and audit artifacts that reflect how an AI system worked months ago….
Fortinet has begun releasing FortiOS versions that fix CVE-2026-24858, a critical zero-day vulnerability that allowed attackers to log into targeted…