Category: HelpnetSecurity
OpenPaX is an open-source kernel patch that mitigates common memory safety errors, re-hardening systems against application-level memory safety attacks using…
Although most organizations use emails with built-in security features that filter out suspicious messages, criminals always find a way to…
Here’s a look at the most interesting products from the past month, featuring releases from: Action1, Balbix, BreachLock, Commvault, Dashlane,…
Sophos conducted defensive and counter-offensive operation over the last five years with multiple interlinked nation-state adversaries based in China targeting…
A supply chain compromise involving Lottie Player, a widely used web component for playing site and app animations, has made…
In this Help Net Security interview, Miguel Guevara, Product Manager, Privacy Safety and Security at Google, discusses the complexities involved…
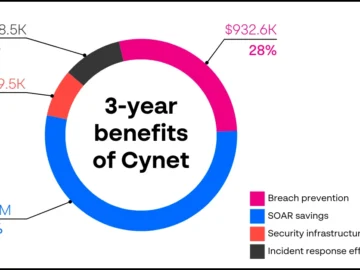
Cost savings and business benefits were quantified in “The Total Economic Impact of Cynet All-in-One Security,” a commissioned study conducted…
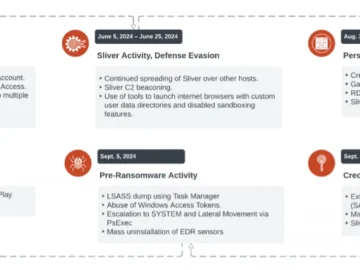
North Korean state-sponsored hackers – Jumpy Pisces, aka Andariel, aka Onyx Sleet – have been spotted burrowing into enterprise systems,…
Yet again, connected devices are in the news for all the wrong reasons. In October, security researchers found that robot…
In this Help Net Security interview, Lior Div, CEO at Seven AI, discusses the concept of agentic AI and its…
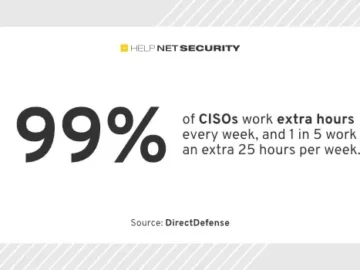
The most common challenge for CISOs is resource constraints: not enough staff, budget or technology to support the security program…
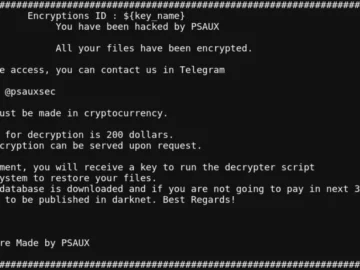
A threat actor – or possibly several – has hit approximately 22,000 vulnerable instances of CyberPanel and encrypted files on…