Category: HelpnetSecurity
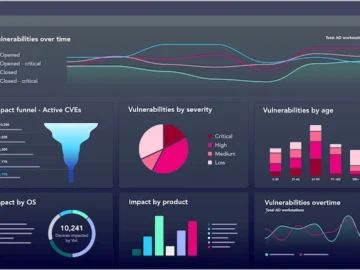
XM Cyber launched its innovative Vulnerability Risk Management (VRM) solution, extending its Continuous Exposure Management Platform. This new approach to…
Neon, the serverless Postgres database built for developers, launched Neon Authorize. It enables developers to manage permissions and access controls…
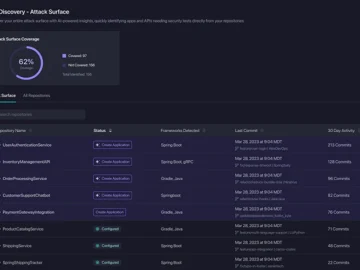
With the proliferation of APIs, and the speed at which AI functionality is helping fuel innovation, a strategic approach for…
Midnight Blizzard – a cyber espionage group that has been linked to the Russian Foreign Intelligence Service (SVR) – is…
In this Help Net Security interview, Carla Roncato, VP of Identity at WatchGuard Technologies, discusses how companies can balance privacy,…
Cybersecurity is an overly reactive industry. Too often we act like firefighters, rushing from blaze to blaze, extinguishing flames hoping…
Medical practices remain vulnerable to cyberattacks, with over a third unable to cite a cybersecurity incident response plan, according to…
Securiti released Gencore AI, a holistic solution to easily build safe, enterprise-grade GenAI systems, copilots and AI agents. This new…
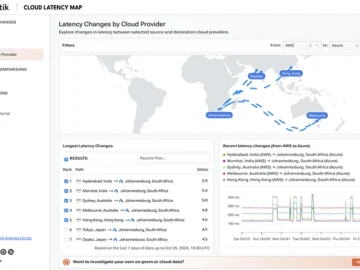
Kentik launched The Cloud Latency Map, a free public tool allowing anyone to explore the latencies measured between over 100…
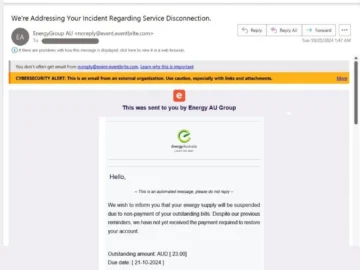
Crooks are leveraging the event management and ticketing website Eventbrite to deliver their phishing emails to potential targets. “Since July,…
API Gateway Security Engineer Ness Technologies | Israel | Hybrid – View job details As an API Gateway Security Engineer,…
Despite two patching attempts, a security issue that may allow attackers to compromise Windows user’s NTLM (authentication) credentials via a…