Category: HelpnetSecurity
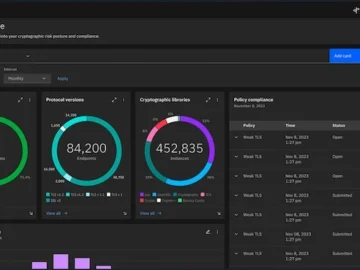
As hybrid cloud-, AI-, and quantum-related risks upend the traditional data security paradigm, IBM is launching IBM Guardium Data Security…
Broadcom has released new patches for previously fixed vulnerabilities (CVE-2024-38812, CVE-2024-38813) in vCenter Server, one of which hasn’t been fully…
Fastly released Fastly DDoS Protection to provide automatic protection from Layer 7 and other application-level DDoS attacks. With a click…
Attackers have exploited an XSS vulnerability (CVE-2024-37383) in the Roundcube Webmail client to target a governmental organization of a CIS…
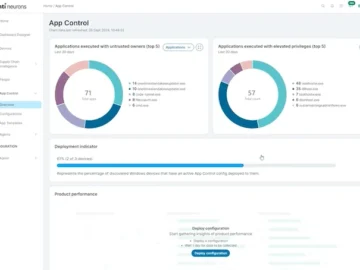
Ivanti introduced Ivanti Neurons for App Control, which safeguards devices from unauthorized applications. In addition, Ivanti released new analytics in…
AI adoption and integration has continued its rapid momentum within the hacking community, according to Bugcrowd. Nevertheless, it continues to…
Phishing scams aimed at voters, malicious domain registrations impersonating candidates, and other threat activity designed to exploit unassuming victims take…
Government information technology leaders find themselves at a challenging balance point: On one end of the scale are increasing threats…
In this Help Net Security interview, Dr Kathryn Jones, Head of School, Computer Science and Informatics at Cardiff University, discusses…
The ultimate guide to AI security: key AI security risks, vulnerabilities and strategies for protection. 61% of companies use AI,…
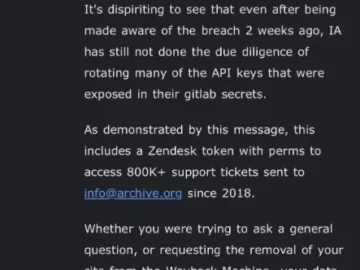
Cybersecurity troubles are not over for the Internet Archive (IA), the nonprofit organization behind the popular digital library site: after…
In this Help Net Security interview, Ian Swanson, CEO of Protect AI, discusses the concept of “secure AI by design.”…