Category: HelpnetSecurity
84% of CISOs believe the role needs to be split into two functions – one technical and one business-focused, to…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: 87,000+ Fortinet devices still open…
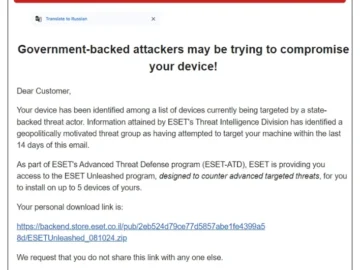
Attackers have tried to deliver wiper malware to employees at organizations across Israel by impersonating cybersecurity company ESET via email….
Law enforcement agencies have arrested suspects involved in cyber attacks claimed by USDoD and Anonymous Sudan, as well as a…
Here’s a look at the most interesting products from the past week, featuring releases from ExtraHop, GitGuardian, Nametag, Okta, Rubrik,…
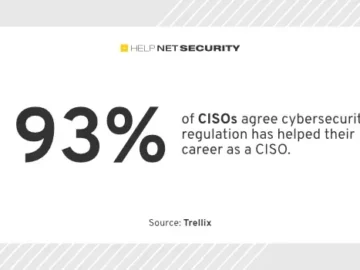
Despite global information security spending projected to reach $215 billion in 2024, 44% of CISOs surveyed reported they were unable…
A lost, stolen, or compromised smartphone today means we are in serious trouble. Most people have everything related to their…
Cybercrime in recent years shows no signs of slowing down, with phishing attacks surging and ransomware tactics becoming more advanced,…
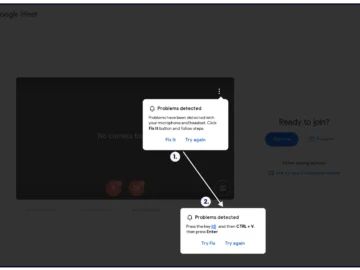
Users of the Google Meet video communication service have been targeted by cyber crooks using the ClickFix tactic to infect…
Cyber-physical devices are increasingly getting compromised and leveraged by criminal groups and state-sponsored threat actors. Fyodor Yarochkin, Senior Threat Solution…
MongoDB Queryable Encryption allows customers to securely encrypt sensitive application data and store it in an encrypted format within the…
GhostStrike is an open-source, advanced cybersecurity tool tailored for ethical hacking and Red Team operations. It incorporates cutting-edge techniques, including…