Category: HelpnetSecurity
More than 50% of executives expect deepfake attacks to increase over the next 12 months, but only 7% report using…
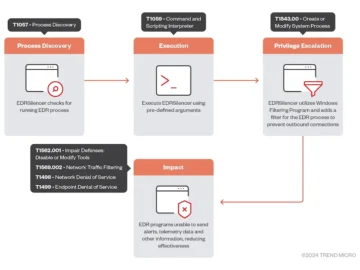
Threat actors are leveraging the open-source EDRSilencer tool to evade endpoint detection and response systems, Trend Micro researchers have noticed….
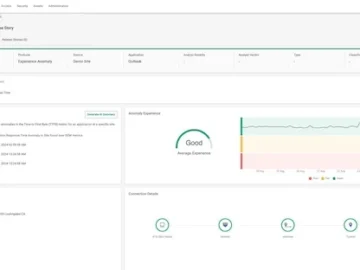
Cato Networks expanded the Cato SASE Cloud Platform by introducing Cato Digital Experience Monitoring (DEM). This announcement is the third…
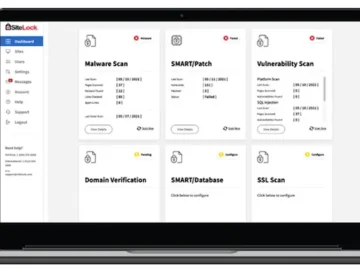
Sectigo announced SiteLock 2.0, a major upgrade to SiteLock, its website security and protection platform. SiteLock 2.0 is designed to…
Last week, CISA added CVE-2024-23113 – a critical vulnerability that allows unauthenticated remote code/command execution on unpatched Fortinet FortiGate firewalls…
An employee is exiting your organization. Regardless of the terms of departure, an ex-staffer has the potential when they leave…
In this Help Net Security interview, Ismael Valenzuela, Vice President of Threat Research & Intelligence at BlackBerry, discusses the impact…
Cyber claims have continued their upwards trend over the past year, driven in large part by a rise in data…
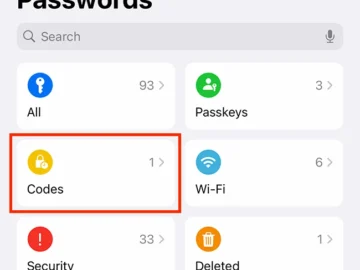
Starting with iOS 18, iPadOS 18, macOS Sequoia, and visionOS 2, the Apple Passwords app enables you to manage your…
Stolen credentials remain the most common cause of a data breach. Various methods exist to prevent such breaches, and the…
We present a list of selected cybersecurity companies that received funding during the third quarter of 2024 (Q3 2024). Apono…
If someone told you five years ago that you could pose questions to an AI agent about the most vexing…