Category: HelpnetSecurity
Governance, risk, and compliance frameworks are critical. They enable cybersecurity professionals to accurately identify an organization’s risk posture, align business…
YARA is a powerful tool designed primarily to aid malware researchers in identifying and categorizing malware samples, though its applications…
In this Help Net Security interview, Emily Wienhold, Cyber Education Specialist at Optiv, discusses how business leaders can promote a…
70% of customer-facing APIs are secured using HTTPS, leaving nearly one-third of these APIs completely unprotected, according to F5. This…
Cloud Cybersecurity Analyst III Texas Health and Human Services | USA | Hybrid – View job details As a Cloud…
For October 2024 Patch Tuesday, Microsoft has released fixes for 117 security vulnerabilities, including two under active exploitation: CVE-2024-43573, a…
Ivanti has patched three additional Cloud Service Appliance (CSA) zero-day flaws, which have been exploited by attackers in conjuction with…
OpenBSD is a free, multi-platform 4.4BSD-based UNIX-like operating system. The 57th release, OpenBSD 7.6, comes with new features, various improvements,…
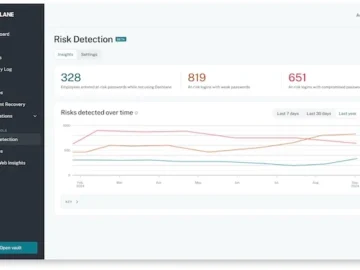
Dashlane launched Credential Risk Detection, a solution that continuously monitors and detects at-risk credential activity in real-time across the workforce,…
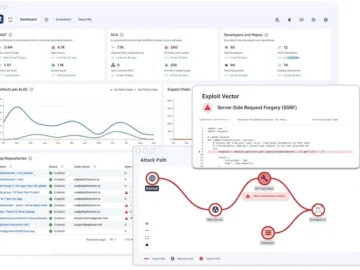
Data Theorem launched Code Secure, the latest evolution in application security designed to protect the software supply chain from code…
An actively exploited zero-day vulnerability (CVE-2024-43047) affecting dozens of Qualcomm’s chipsets has been patched by the American semiconductor giant. About…
American Water, the largest water and wastewater utility company in the US, has shut down some of its systems following…