Category: HelpnetSecurity
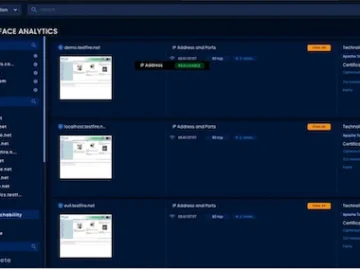
BreachLock strengthens continuous threat exposure management (CTEM) capabilities for enterprise customers with its new Attack Surface Analytics feature. Time is…
As personal data becomes increasingly commodified and centralized, the need for individuals to reclaim control over their identities has never…
In this Help Net Security interview, Brian Pontarelli, CEO at FusionAuth, discusses the evolving authentication challenges posed by the rise…
The discovery that 95% of advanced bot attacks go undetected points to a weakness in current detection and mitigation strategies….
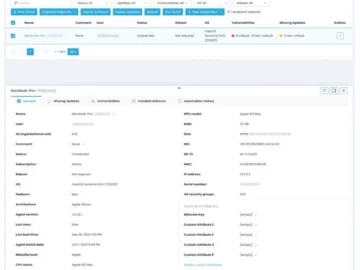
Action1 announced its latest product release. As part of its platform enhancements, Action1 has introduced a new agent for macOS,…
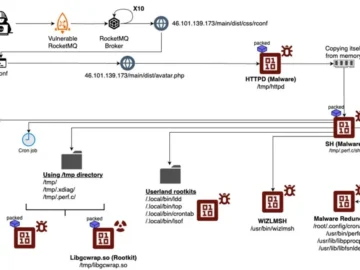
Thousands of Linux systems are likely infected with the highly elusive and persistent “perfctl” (or “perfcc“) cryptomining malware and many…
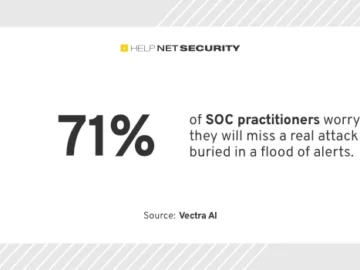
Security operations center (SOC) practitioners believe they are losing the battle detecting and prioritizing real threats – due to too…
For several years, external attack surface management (EASM) has been an important focus for many security organizations and the vendors…
In this Help Net Security interview, Amiram Shachar, CEO at Upwind, discusses the complexities of cloud security in hybrid and…
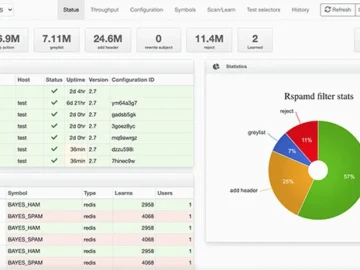
Rspamd is an open-source spam filtering and email processing framework designed to evaluate messages based on a wide range of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: October 2024 Patch Tuesday forecast:…
Microsoft and the US Justice Department have seized over 100 domains used by Star Blizzard, a Russian nation-state threat actor….