Category: HelpnetSecurity
MaLDAPtive is an open-source framework for LDAP SearchFilter parsing, obfuscation, deobfuscation, and detection. At its core, the project features a…
October arrived, and Microsoft started the month by announcing the release of Windows 11 24H2. The preview versions of this…
In this Help Net Security interview, Sanaz Yashar, CEO at Zafran, discusses the role of threat exposure management (TEM) in…
Off-the-shelf offensive security tools and poorly configured cloud environments create openings in the attack surface, according to Elastic. Adversaries are…
Here’s a look at the most interesting products from the past week, featuring releases from Balbix, Halcyon, Metomic, Red Sift,…
CVE-2024-29824, an unauthenticated SQL Injection vulnerability in Ivanti Endpoint Manager (EPM) appliances, is being exploited by attackers, the Cybersecurity and…
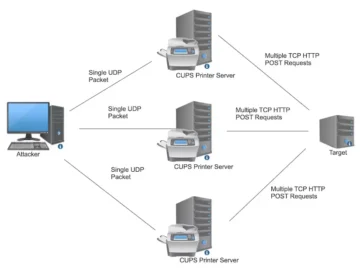
While the Common UNIX Printing System (CUPS) vulnerabilities recently disclosed by researcher Simone “evilsocket” Margaritelli are not easily exploited for…
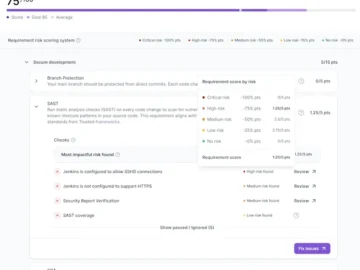
Legit Security launched its new “Legit Posture Score,” delivering a dynamic, comprehensive, and fully transparent ASPM rating system. Now security…
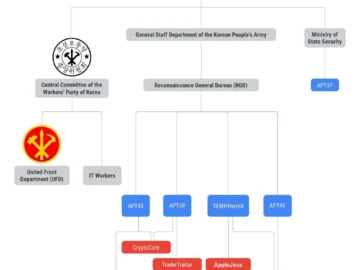
Undeterred by the indictment issued against one of its alleged members, North Korean APT group Stonefly (aka APT45) continues to…
The cybersecurity skills gap presents ongoing challenges worldwide, so organizations are scrambling to fill cloud security positions. Having a subject…
The latest Apple OS updates (iOS 18, iPadOS 18, macOS Sequoia) have introduced a standalone Passwords app, to make users’…
The latest Apple OS updates (iOS 18, iPadOS 18, macOS Sequoia) have introduced a standalone Passwords app, to make users’…