Category: HelpnetSecurity
Despite the rise in cyber threats, many people do not have a holistic view of security, according to Yubico. The…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Windows Server 2025 gets hotpatching…
Tosint is an open-source Telegram OSINT tool that extracts useful information from Telegram bots and channels. It’s suited for security…
IoT devices have become integral to how many organizations operate. From Smart TVs in conference rooms to connected sensors and…
In this Help Net Security interview, Nadir Izrael, CTO at Armis, discusses how AI has transformed cyberwarfare by amplifying attacks’…
Here’s a look at the most interesting products from the past week, featuring releases from Absolute, ArmorCode, Bitdefender, Guardsquare, Malwarebytes,…
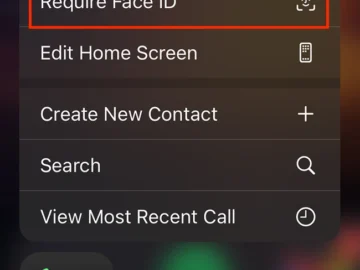
iOS 18 allows you to lock and hide apps to protect the information within them by requiring Face ID, Touch…
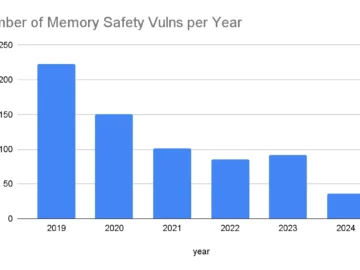
Google’s decision to write new code into Android’s codebase in Rust, a memory-safe programming language, has resulted in a significant…
Deep-learning models have found applications across various industries, from healthcare diagnostics to financial forecasting. However, their high computational demands often…
In July, Wall Street experienced its worst day since 2022, with the tech-focused Nasdaq falling by 3.6%. The downturn was…
In this Help Net Security interview, Andrius Buinovskis, Head of Product at NordLayer, discusses how organizations can assess their compliance…
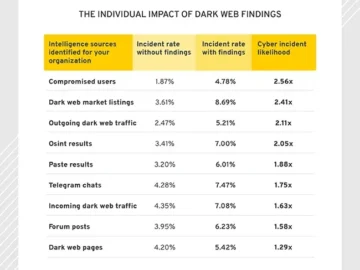
The presence of any data relating to an organization on the dark web demonstrably increases its risk of a cyber…