Category: HelpnetSecurity
NETGEAR expanded its Nighthawk WiFi 7 standalone router line to include the new RS600, RS500, and RS200. The lineup of…
Telegram will start handing over the IP addresses and phone numbers of users who violate their Terms of Service “to…
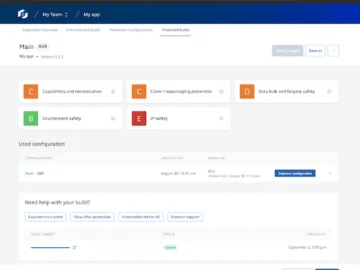
Guardsquare announced an innovative, guided approach to mobile application security that empowers teams to achieve the highest level of protection…
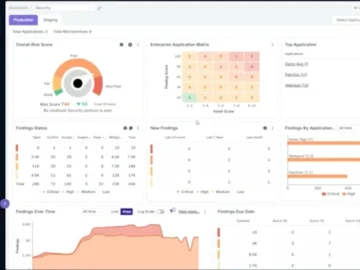
ArmorCode announced the expansion of its platform with the launch of two new modules for Penetration Testing Management and Exceptions…
In this Help Net Security interview, Jon France, CISO at ISC2, discusses cybersecurity workforce growth. He outlines organizations’ challenges, such…
Recent reports underscore increased fraud losses driven by both old methods and new technologies. As fraudsters exploit advancements in AI…
Companies across industries are seeing more bot-driven attacks, both basic and advanced, according to DataDome. An analysis of over 14,000…
Ransomware is seen as the biggest cybersecurity threat across every industry, with 75% of organizations affected by ransomware more than…
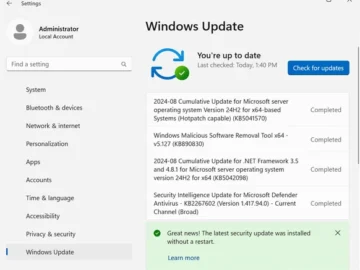
Organizations that plan to upgrade to Windows Server 2025 once it becomes generally available will be able to implement some…
More often than not, a cyber attack or a cyber incident that results in business disruption will spur organizations to…
In this Help Net Security interview, Christopher Jones, Chief Technology Officer and Chief Data Officer at Nightwing, talks about some…
Certainly is an open-source offensive security toolkit designed to capture extensive traffic across various network protocols in bit-flip and typosquatting…