Category: HelpnetSecurity
In the push for secure AI models, many organizations have turned to differential privacy. But is the very tool meant…
In this Help Net Security interview, Alex Spivakovsky, VP of Research & Cybersecurity at Pentera, discusses essential metrics for evaluating…
Data breach episodes have been constantly rising with the number of data breach victims crossing 1 billion in the first…
92% of security leaders have concerns about the use of AI-generated code within their organization, according to Venafi. Tension between…
Firms in the construction industry are getting breached by hackers via internet-exposed servers running Foundation accounting software, Huntress researchers are…
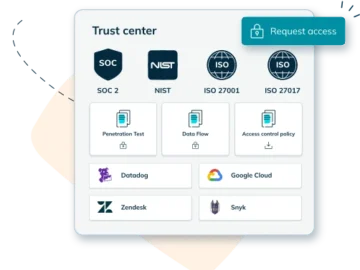
anecdotes has launched Anecdotes Trust Center, a centralized platform for companies to effortlessly share compliance and security information and documentation…
Another encrypted communication platform used by criminals has been dismantled and its alleged mastermind arrested, the Australian Federal Police has…
Broadcom has released fixes for two vulnerabilities affecting VMware vCenter Server that can be triggered by sending a specially crafted…
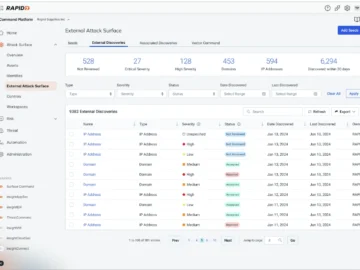
Rapid7 has unveiled Vector Command, a fully-managed offensive security service. Vector Command combines the external attack surface assessment capabilities of…
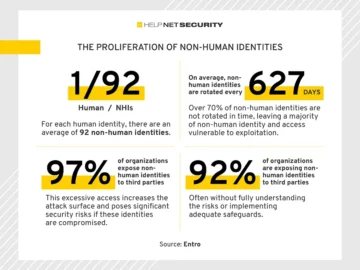
97% of non-human identities (NHIs) have excessive privileges, increasing unauthorized access and broadening the attack surface, according to Entro Security’s…
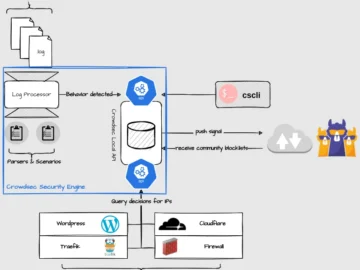
Crowdsec is an open-source solution that offers crowdsourced protection against malicious IPs. CrowdSec features For this project, the developers have…
In this Help Net Security interview, Henrik Plate, CISSP, security researcher, Endor Labs, discusses the complexities AppSec teams face in…