Category: HelpnetSecurity
Application Security Engineer CHANEL | France | On-site – View job details As an Application Security Engineer, you will perform…
Organizations are combating excessive remote access demands with an equally excessive number of tools that provide varying degrees of security,…
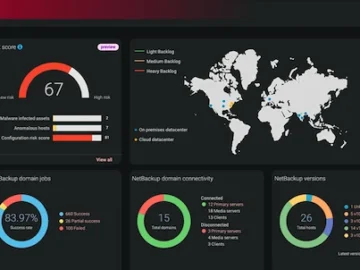
Veritas Technologies unveiled new AI-driven capabilities to further expand the strength and functionality of the Veritas cyber resilience portfolio. The…
Apple has launched iOS 18, the latest significant iteration of the operating system powering its iPhones. Along with many new…
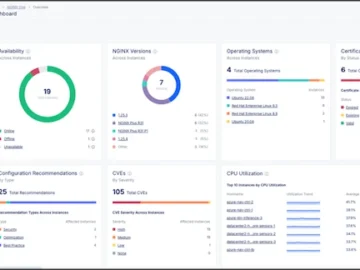
F5 launched F5 NGINX One, combining advanced load balancing, web and application server capabilities, API gateway functionalities, and security features…
CVE-2024-8190, an OS command injection vulnerability in Ivanti Cloud Services Appliance (CSA) v4.6, is under active exploitation. Details about the…
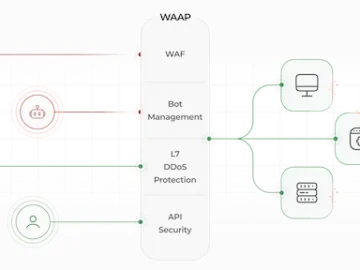
Gcore launched Gcore WAAP, its end-to-end web application and API protection solution. Leveraging AI capabilities, Gcore WAAP integrates four products…
Service accounts are non-human identities used to automate machine-to-machine interactions. They support critical functions – such as running scripts, services,…
In this Help Net Security interview, Robert Ramsey, CEO at Rain Technology, discusses the growing threat of visual hacking, how…
The global cybersecurity workforce gap reached a new high with an estimated 4.8 million professionals needed to effectively secure organizations,…
The cyber insurance market is set for explosive growth as organizations increasingly seek financial protection against rising cyber threats. This…
EchoStrike is an open-source tool designed to generate undetectable reverse shells and execute process injection on Windows systems. “EchoStrike allows…