Category: HelpnetSecurity
LOKKER released a new consent management solution available in its Privacy Edge Platform. This builds on LOKKER’s earlier release of…
September 2024 Patch Tuesday is here and Microsoft has delivered 79 fixes, including those for a handful of zero-days (CVE-2024-38217,…
Ketch launched its product suite for digital media brands. The digital media industry faces increasing challenges. Intense FTC scrutiny on…
The US Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2024-40766 – a recently fixed improper access control vulnerability affecting…
Open-source cybersecurity tools provide transparency and flexibility, allowing users to examine and customize the source code to fit specific security…
In this Help Net Security interview, Shane Cox, Director, Cyber Fusion Center at MorganFranklin Consulting, discusses the evolving methodologies and…
Users of Zyxel network-attached storage (NAS) devices are urged to implement hotfixes addressing a critical and easily exploited command injection…
Wing Security has released SaaS Pulse, a free tool for SaaS security management, offering organizations actionable insights and continuous oversight…
Huntress announces the arrival of its new Managed SIEM solution, designed to serve small—to mid-sized enterprises and their MSP allies…
Crashes due to faulty updates are nothing new; in fact, one reason IT teams often delay updates is their unreliability…
CVE-2024-40711, a critical vulnerability affecting Veeam Backup & Replication (VBR), could soon be exploited by attackers to steal enterprise data….
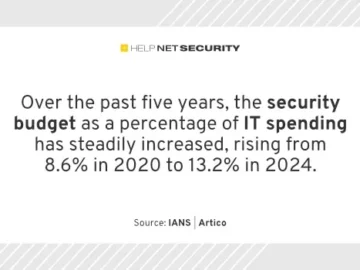
Amidst global economic and geopolitical uncertainty, markets are jittery, companies are spending frugally, and investors remain cautious, according to IANS…