Category: HelpnetSecurity
In this Help Net Security interview, Umaimah Khan, CEO of Opal Security, shares her insights on implementing the Principle of…
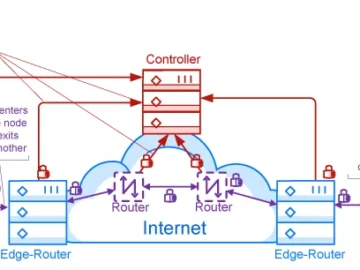
OpenZiti is a free, open-source project that embeds zero-trust networking principles directly into applications. Example of an OpenZiti overlay network…
Cybercriminals are beginning to take advantage of the new malicious options that large language models (LLMs) offer them. LLMs make…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Vulnerability allows Yubico security keys…
The US Department of Justice has named five Russian computer hackers as members of Unit 29155 – i.e., the 161st…
For the fourth time in the last five months, Apache OFBiz users have been advised to upgrade their installations to…
Resecurity announced its recognition in the prestigious Frost & Sullivan’s Global Cyber Threat Intelligence 2024 report. This annual report is…
As cybercriminals continue to refine their methods, blending traditional strategies with new technologies, the financial toll on individuals and organizations…
Businesses run on SaaS solutions: nearly every business function relies on multiple cloud-based tech platforms and collaborative work tools like…
I asked for a calm August 2024 Patch Tuesday in last month’s forecast article and that came to pass. The…
Respotter is an open-source honeypot designed to detect attackers when they launch Responder within your environment. This application identifies active…
Ransomware is an all-too-common occurrence: 83% of organizations have experienced at least one ransomware attack in the last year, 46%…