Category: HelpnetSecurity
The threat of deepfakes lies not in the technology itself, but in people’s natural tendency to trust what they see….
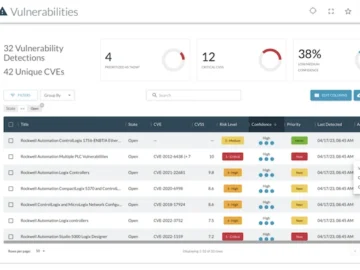
Dragos announced the latest release of the Dragos Platform, an OT network visibility and cybersecurity platform. The updates provide industrial…
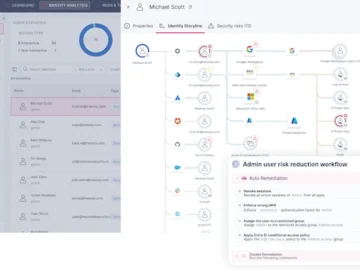
Rezonate announced a new identity security solution for mid-market companies. The offering proactively reduces the identity attack surface and improves…
Organizations using Fortra’s FileCatalyst Workflow are urged to upgrade their instances, so that attackers can’t access an internal HSQL database…
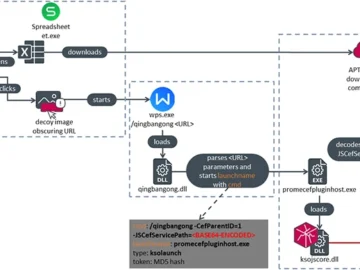
ESET researchers discovered a remote code execution vulnerability in WPS Office for Windows (CVE-2024-7262). APT-C-60, a South Korea-aligned cyberespionage group,…
BlackByte, the ransomware-as-a-service gang believed to be one of Conti’s splinter groups, has (once again) created a new iteration of…
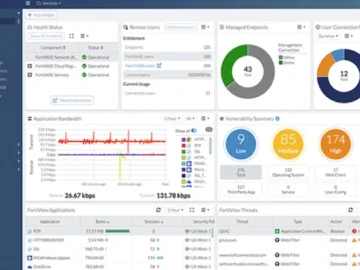
Fortinet announced the addition of sovereign SASE and GenAI capabilities to its unified SASE solution. Fortinet Unified SASE provides complete…
HYCU announced significant updates to its HYCU R-Cloud data protection platform that offers customers additional protection for their Identity and…
Business Information Security Officer Toyota North America | USA | On-site – View job details Acting as an Information Security…
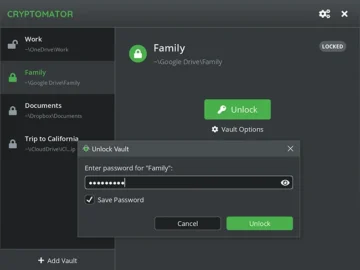
Cryptomator offers open-source, client-side encryption of your files in the cloud. It’s available for Windows, Linux, macOS and iOS. Cryptomator…
Cybercriminals are capitalizing on the travel and hospitality industry’s peak season, using increased traffic as cover for their attacks, according…
GenAI, deepfakes and cybercrime are critical threats putting intensifying pressures on businesses, according to Experian. Top online security concerns for…