Category: HelpnetSecurity
After peaking in late 2023, the ransomware industry is beginning to stabilize in productivity, with notable developments in ransomware targets,…
To date, most technology solutions focused on vulnerability management have focused on the prioritization of risks. That usually took the…
In the first six months of 2024, Hiya flagged nearly 20 billion calls as suspected spam – more than 107…
Here’s a look at the most interesting products from the past week, featuring releases from Entrust, Fortanix, McAfee, Own, RightCrowd,…
QNAP has released the QTS 5.2 NAS operating system. A standout feature of this release is the debut of Security…
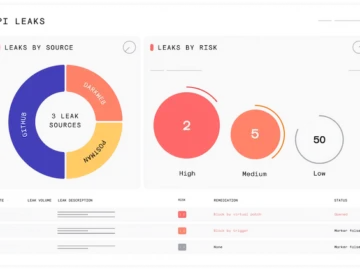
Wallarm announced its latest innovation: API Attack Surface Management (AASM). This agentless technology transforms how organizations identify, analyze, and secure…
A critical vulnerability (CVE-2024-6800) affecting all currently supported versions of GitHub Enterprise Server (GHES) may allow attackers to gain unrestricted…
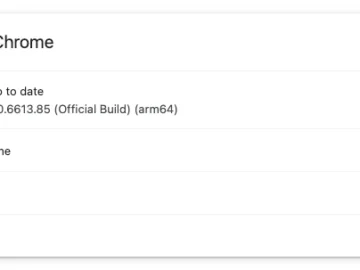
A new Chrome zero-day vulnerability (CVE-2024-7971) exploited by attackers in the wild has been fixed by Google. About CVE-2024-7971 CVE-2024-7971…
ESET researchers uncovered NGate malware, which can relay data from victims’ payment cards via a malicious app installed on their…
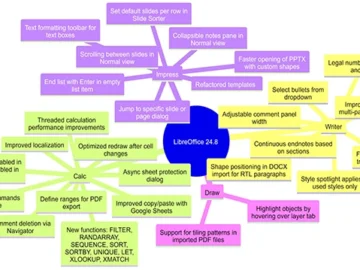
LibreOffice 24.8, the new major release of the free Windows, macOS, and Linux office suite, is now available. This is…
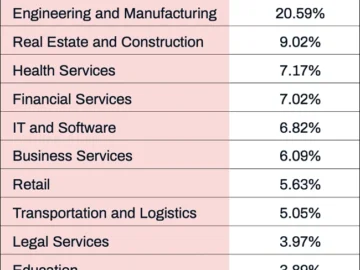
Senior executives are prime targets for cybercriminals, with 72% of surveyed cybersecurity professionals in the US reporting that cyberattacks have…
Things change fast in the world of data privacy. Just earlier this year, the question I was being asked most…