Category: HelpnetSecurity
Threat actors use popular file-hosting or e-signature solutions as a disguise to manipulate their targets into revealing private information or…
Culture is a catalyst for security success. It can significantly reduce cybersecurity risks and boost cybersecurity resilience of any organization….
In this Help Net Security interview, Kyle Wickert, Worldwide Strategic Architect at AlgoSec, discusses the role of AI in application…
The risk of deepfakes is rising with 47% of organizations having encountered a deepfake and 70% of them believing deepfake…
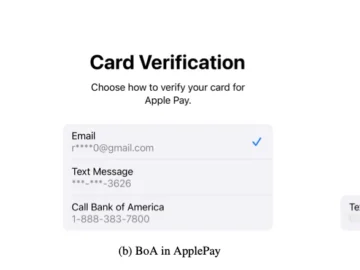
Fraudsters can add stolen payment cards to digital wallet apps and continue making online purchases even after victims’ report the…
Own released Continuous Data Protection for Salesforce customers, further strengthening its product offering to include recovery and analysis capabilities. Own…
Effectively converging, managing and using enterprise data is a huge undertaking. Enterprises have vast hoards of data, but those hoards…
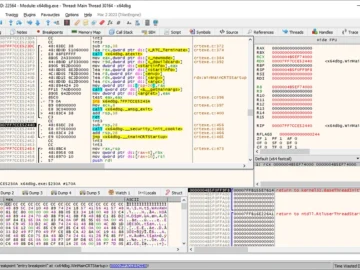
x64dbg is an open-source binary debugger for Windows, designed for malware analysis and reverse engineering of executables without access to…
Despite their role in connecting applications and driving innovation, APIs often suffer from serious security vulnerabilities. Recent investigations reveal that…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Unpatched MS Office flaw may…
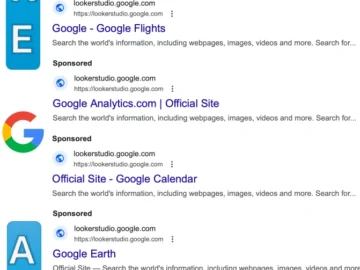
Google Search ads that target users looking for Google’s own services lead them to spoofed sites and Microsoft and Apple…
I recently spent six days in Las Vegas attending DEF CON, BsidesLV, and Black Hat USA 2024, where I had…