Category: HelpnetSecurity
Browser extensions are a prime target for cybercriminals. And this isn’t just a consumer problem – it’s a new frontier…
C-suite executives face a unique challenge: aligning their priorities between driving technological innovation and ensuring business resilience while managing ever-evolving…
Nightfall AI’s research revealed that secrets like passwords and API keys were most often found in GitHub, with nearly 350…
A widespread campaign featuring a malicious installer that saddles users with difficult-to-remove malicious Chrome and Edge browser extensions has been…
A new MS Office zero-day vulnerability (CVE-2024-38200) can be exploited by attackers to grab users’ NTLM hashes, Microsoft has shared…
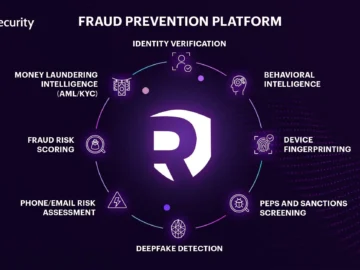
Resecurity unveiled its advanced AI-driven Fraud Prevention Platform. This versatile solution is engineered to combat fraud across banking, virtual asset…
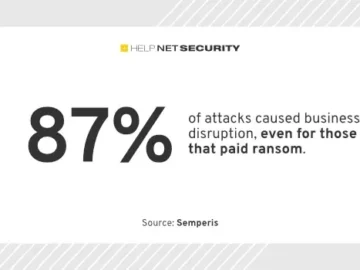
An alarming trend toward multiple, sometimes simultaneous cyber attacks forces business leaders to re-evaluate their cyber resilience strategies to address…
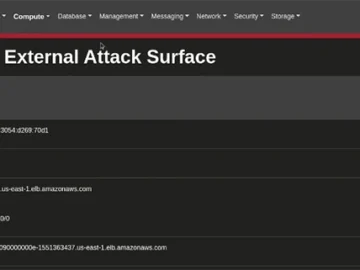
Scout Suite is an open-source, multi-cloud security auditing tool designed to assess the security posture of cloud environments. By leveraging…
Traditional cloud security issues often associated with cloud service providers (CSPs) are continuing to decrease in importance, according to the…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: August 2024 Patch Tuesday forecast:…
July ended up being more ‘exciting’ than many of us wanted; we’re supposed to be in the height of summer…
A “0.0.0.0-Day” vulnerability affecting Chrome, Safari and Firefox can be – and has been – exploited by attackers to gain…