Category: HelpnetSecurity
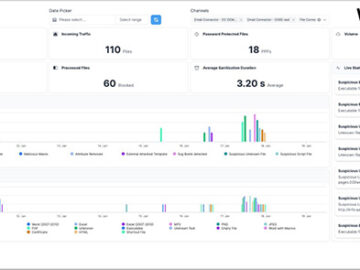
Security operation centers (SOCs) need to be better equipped to manage the sheer scale of data to monitor and the…
As businesses strive to protect their data and privacy, the demand for skilled cybersecurity professionals continues to grow. This article…
In this Help Net Security video, Beth Miller, Field CISO at Code42, highlights a significant trend: 73% of life sciences…
Once a peripheral concern, OT security has become a mandatory focus for organizations worldwide, according to Cisco’s report. The report…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Why a strong patch management…
Votiro expanded the privacy toolsets and integrations within its DDR platform. New features include the ability to mask privacy data…
Here’s a look at the most interesting products from the past week, featuring releases from: Adaptive Shield, Fortanix, Clutch Security,…
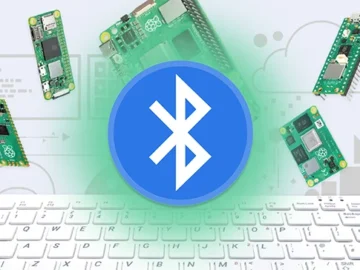
Remote.It released its open-source project to enable Raspberry Pi Bluetooth (BLE) Wi-Fi network configuration. The project allows a computer or…
Ransomware attacks have reached new heights of ambition and audacity over the past year, marked by a notable surge in…
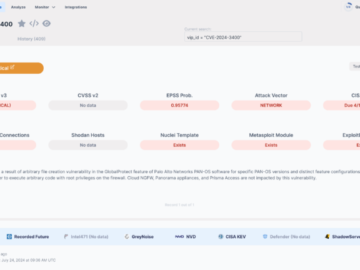
40% of tested environments allowed attack paths that lead to domain admin access, according to Picus Security. Achieving domain admin…
Nucleus Security has launched its Nucleus Vulnerability Intelligence Platform. Platform enables enterprises to aggregate, analyze, and act on insights from…
Wing Security launched its new tailored SaaS Threat Intelligence, providing organizations with personalized detection and response capabilities directly integrated into…