Category: HelpnetSecurity
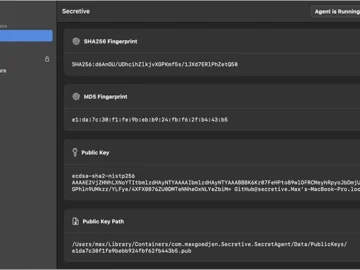
Secretive is an open-source, user-friendly app designed to store and manage SSH keys within the Secure Enclave. Typically, SSH keys…
Cloud Security Architect Precisely | United Kingdom | Remote – View job details As a Cloud Security Architect, you will…
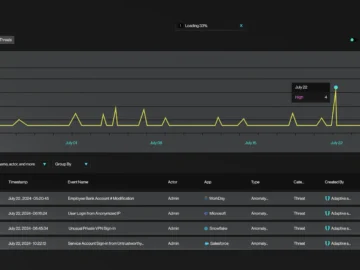
Adaptive Shield has unveiled its Identity Threat Detection & Response (ITDR) platform for SaaS environments. The recent Snowflake breach served…
IBM released its annual Cost of a Data Breach Report revealing the global average cost of a data breach reached…
Safety and quality are not features that can be added through testing — they must be integral to the design….
Although endpoint anti-malware and other security controls are now standard at the operating system level, keeping all endpoint software up-to-date…
In this Help Net Security interview, Grant Geyer, Chief Strategy Officer at Claroty, discusses the prevalent vulnerabilities in Windows-based engineering…
Healthcare organizations continue to put their business and patients at risk of exposing their most sensitive data, according to Metomic….
Estimated financial losses due to the recent massive IT outage triggered by the faulty CrowdStrike update are counted in billions,…
CVE-2023-45249, a critical vulnerability affecting older versions of Acronis Cyber Infrastructure, is being exploited by attackers. About Acronis Cyber Infrastructure…
More organizations rely on cloud platforms to reap the benefits of scalability, flexibility, availability, and reduced costs. However, cloud environments…
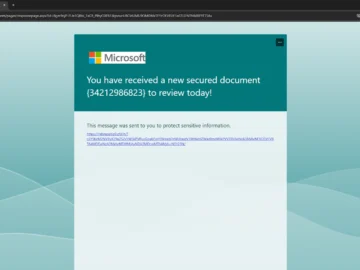
There has been an uptick in phishing campaigns leveraging Microsoft Forms this month, aiming to trick targets into sharing their…