Category: HelpnetSecurity
BIND (Berkeley Internet Name Domain) is an open-source DNS software system with an authoritative server, a recursive resolver, and related…
Somewhere, right now, a CISO is in a boardroom making their best case for stronger identity threat detection and response…
In this Help Net Security interview, Ava Chawla, Head of Cloud Security at AlgoSec, discusses the most significant cloud security…
Regulated data (data that organizations have a legal duty to protect) makes up more than a third of the sensitive…
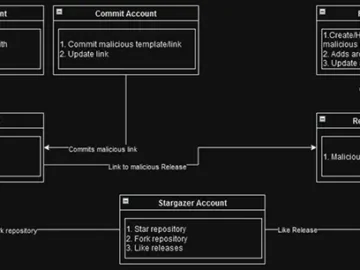
Check Point researchers have unearthed an extensive network of GitHub accounts that they believe provides malware and phishing link Distribution-as-a-Service….
A bug in the Content Validator – a software element CrowdStrike relies on for testing and validating Rapid Response Content…
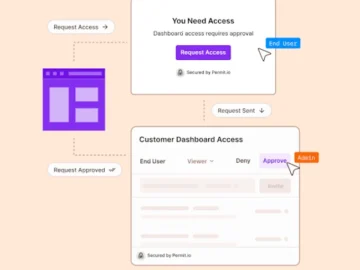
Secure collaboration through access-sharing is a must-have feature in almost any modern application, from requesting to edit a document or…
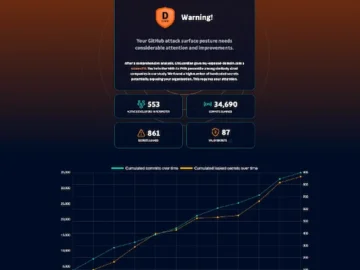
GitGuardian releases a tool to help companies discover how many secrets their developers have leaked on public GitHub, both company-related…
Applied Cryptographer Quantstamp | EMEA | Remote – View job details As an Applied Cryptographer, you will research about various…
In this Help Net Security interview, Karthik Swarnam, Chief Security and Trust Officer at ArmorCode, discusses key metrics and KPIs…
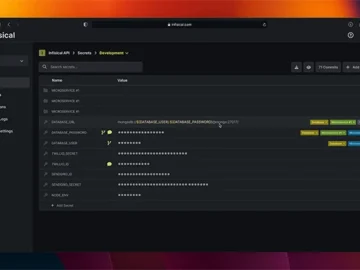
Infisical is an open-source secret management platform developers use to centralize application configurations and secrets, such as API keys and…
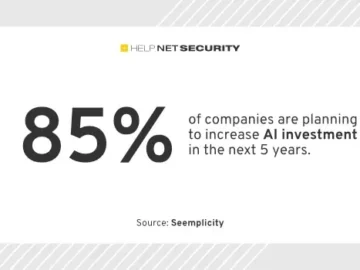
91% of respondents say their security budget is increasing this year, demonstrating a growing recognition of the importance of cybersecurity…