Category: HelpnetSecurity
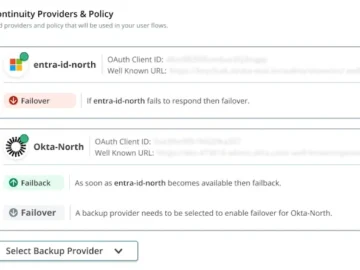
Strata Identity announced Identity Continuity, an addition to its Maverics Identity Orchestration platform. This new premium offering ensures business continuity…
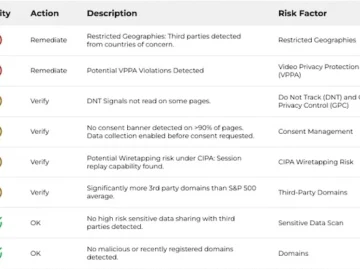
LOKKER released a new privacy solution for insurers: the ability to share on-demand web privacy risk reports with their insureds….
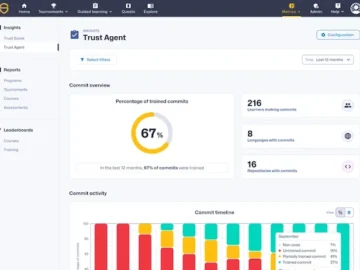
Secure Code Warrior introduced SCW Trust Agent – a solution that assesses the specific security competencies of developers for every…
When it comes to the cyber threat landscape, change is the only constant: the inevitable interplay between cybercriminals and law…
In this Help Net Security interview, Anand Pashupathy, VP & GM, Security Software & Services Division at Intel, explains how…
The fintech market is experiencing a swift transformation driven by emerging technologies like Open Finance and GenAI, as highlighted by…
ESET researchers discovered a zero-day exploit, which targets the Telegram app for Android, that appeared for sale for an unspecified…
As organizations increasingly adopt third-party AI tools to streamline operations and gain a competitive edge, they also invite a host…
By now, most people are aware of – or have been personally affected by – the largest IT outage the…
In this Help Net Security interview, Saira Jesani, Executive Director of the Data & Trust Alliance, discusses the role of…
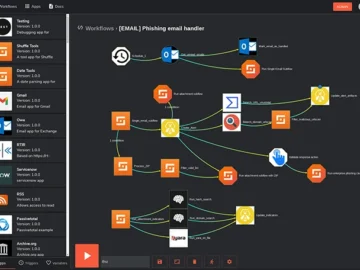
Shuffle is an open-source automation platform designed by and for security professionals. While security operations are inherently complex, Shuffle simplifies…
ESET Research has discovered a sophisticated Chinese browser injector: a signed, vulnerable, ad-injecting driver from a mysterious Chinese company. This…