Category: HelpnetSecurity
Applied Cryptographer Quantstamp | EMEA | Remote – View job details As an Applied Cryptographer, you will research about various…
In this Help Net Security interview, Karthik Swarnam, Chief Security and Trust Officer at ArmorCode, discusses key metrics and KPIs…
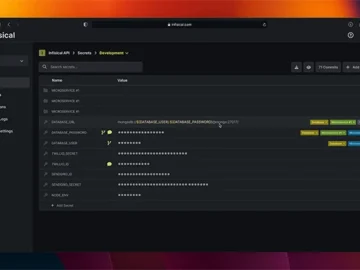
Infisical is an open-source secret management platform developers use to centralize application configurations and secrets, such as API keys and…
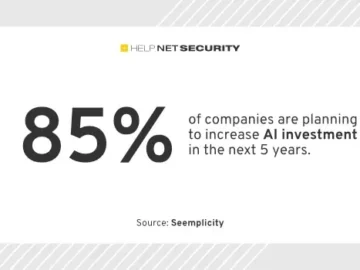
91% of respondents say their security budget is increasing this year, demonstrating a growing recognition of the importance of cybersecurity…
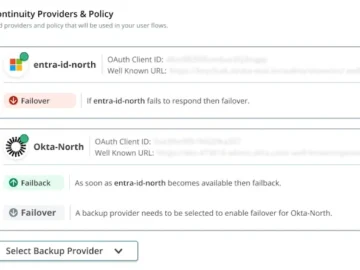
Strata Identity announced Identity Continuity, an addition to its Maverics Identity Orchestration platform. This new premium offering ensures business continuity…
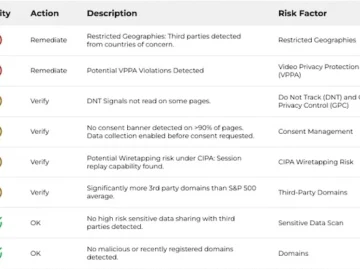
LOKKER released a new privacy solution for insurers: the ability to share on-demand web privacy risk reports with their insureds….
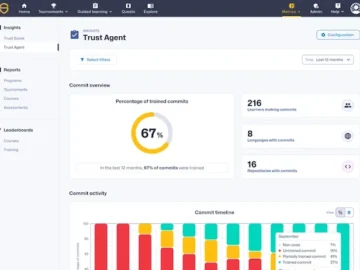
Secure Code Warrior introduced SCW Trust Agent – a solution that assesses the specific security competencies of developers for every…
When it comes to the cyber threat landscape, change is the only constant: the inevitable interplay between cybercriminals and law…
In this Help Net Security interview, Anand Pashupathy, VP & GM, Security Software & Services Division at Intel, explains how…
The fintech market is experiencing a swift transformation driven by emerging technologies like Open Finance and GenAI, as highlighted by…
ESET researchers discovered a zero-day exploit, which targets the Telegram app for Android, that appeared for sale for an unspecified…
As organizations increasingly adopt third-party AI tools to streamline operations and gain a competitive edge, they also invite a host…