Category: HelpnetSecurity
Grype is an open-source vulnerability scanner designed for container images and filesystems that seamlessly integrates with Syft, a powerful Software…
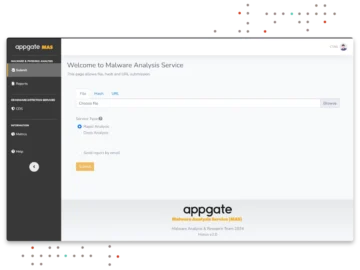
Appgate has unveiled its new Malware Analysis Service that mitigates cyberthreats for enterprises and government agencies by identifying and neutralizing…
Invicti announced Invicti API Security, merging comprehensive API discovery with proactive security testing into a single solution. The growth of…
Most GitHub Actions are susceptible to exploitation; they are overly privileged or have risky dependencies, according to Legit Security. GitHub…
In this Help Net Security, Ankita Gupta, CEO at Akto, discusses API security best practices, advocating for authentication protocols like…
SubSnipe is an open-source, multi-threaded tool to help find subdomains vulnerable to takeover. It’s simpler, produces better output, and has…
Adversary Emulation Team Member Australian Federal Police | Australia | On-site – View job details As an Adversary Emulation Team…
The Cloud Security Alliance (CSA) demonstrated its commitment to improving its vendor-neutral cloud security training with the release of the…
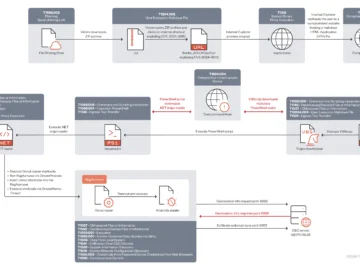
The zero-day exploit used to leverage CVE-2024-38112, a recently patched Windows MSHTML vulnerability, was wielded by an APT group dubbed…
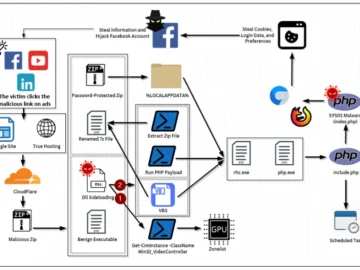
Malicious Google ads are a well known threat, but malvertising can also be found on other popular online destinations such…
A smartphone’s unique Bluetooth fingerprint could be used to track the device’s user–until now. A team of researchers has developed…
It’s been less than 18 months since the public introduction of ChatGPT, which gained 100 million users in less than…