Category: HelpnetSecurity
Most organizations focus on securing routers, servers, firewalls, and other endpoints, but threats can also arise from unfamiliar sources such…
Personal information of over 2,3 million individuals has been stolen by attackers as part of the massive data grab via…
Hackers leveraging stolen Snowflake account credentials have stolen records of calls and texts made by “nearly all” of AT&T’s cellular…
Do you use Authy for your multi-factor authentication needs? If you do, you should keep an eye out for phishing…
Prompt Security announced its product and go-to-market support for Managed Security Service Providers (MSSPs). This strategic initiative has already resulted…
With terms like “AI washing” making their way into mainstream business consciousness, the hype surrounding AI is making it harder…
In this Help Net Security interview, Chaim Mazal, Chief Security Officer at Gigamon, discusses cybersecurity preparedness measures for businesses, the…
This article compiles excerpts from various reports, presenting statistics and insights that could be helpful for CISOs. CISOs becoming more…
Pentera announced a major update to its RansomwareReady product, enabling customers to proactively test the security of their Linux environments….
The US Justice Department (DoJ) has seized two US-based domains used by Russian threat actors to create fake profiles on…
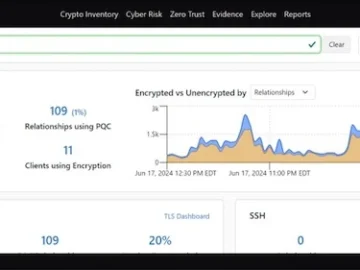
Quantum Xchange announced the latest release of CipherInsights, the company’s network monitoring, crypto-discovery and risk assessment tool. Version 11.0 includes…
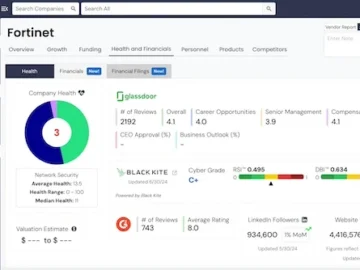
IT-Harvest announced the integration of Black Kite‘s cyber third-party risk intelligence into the IT-Harvest Dashboard. This collaboration provides users with…