Category: HelpnetSecurity
Organizations continue to struggle in detecting breaches as they become more targeted and sophisticated, with more than 1 out of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: The rise of SaaS security…
A vulnerability (CVE-2024-0762) in the Phoenix SecureCore UEFI, which runs on various Intel processors, could be exploited locally to escalate…
The US Department of Commerce has announced an upcoming US-wide ban of cybersecurity and antivirus software by Kaspersky, as its…
A Panaseer investigation into organizations’ annual 10-K filings reported to the SEC shows that from January-May 2024, at least 1,327…
Cilium is an open-source, cloud-native solution that leverages eBPF technology in the Linux kernel to provide, secure, and monitor network…
Here’s a look at the most interesting products from the past week, featuring releases from Atsign, Datadog, Metomic, NinjaOne, Verimatrix,…
Ohio-based Crown Equipment, which is among the largest industrial and forklift truck manufacturers in the world, has become a victim…
CDK Global, a software-as-a-service (SaaS) provider for car dealers and auto equipment manufacturers, has suffered a cyberattack that has temporarily…
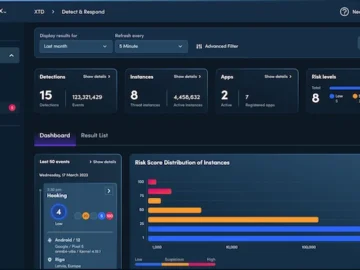
Verimatrix announced major enhancements to its XTD dashboard, providing customers with better visibility into application security risks and more actionable…
Password security has seen dramatic shifts driven by the escalation of cyber threats and technological advancements. This eBook covers: Best…
Organizations have made progress in the past 12 months related to advancing their OT security posture, but there are still…