Category: HelpnetSecurity
In this Help Net Security interview, Julianna Lamb, Stytch CTO, discusses the advantages of passwordless authentication. Eliminating passwords reduces data…
Cybersecurity and infosecurity professionals say that work-related stress, fatigue, and burnout are making them less productive, including taking extended sick…
Cryptocurrency users are being targeted with legitimate-looking but fake apps that deliver information-stealing malware instead, Recorder Future’s researchers are warning….
Managing cybersecurity for any organization is no easy feat. Improving cybersecurity maturity is often even more difficult, made increasingly challenging…
This article compiles excerpts from various reports, presenting statistics and insights on cybersecurity threats faced by businesses and individuals alike….
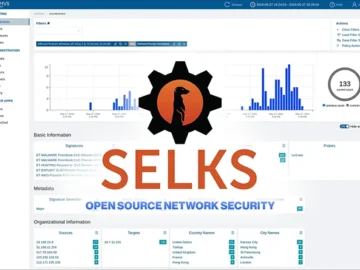
SELKS is a free, open-source, turnkey solution for Suricata-based network intrusion detection and protection (IDS/IPS), network security monitoring (NSM), and…
Application Penetration Tester ShiftCode Analytics | USA | On-site – View job details As an Application Penetration Tester, you will…
Action1 researchers found an alarming increase in the total number of vulnerabilities across all enterprise software categories. “With the NVD’s…
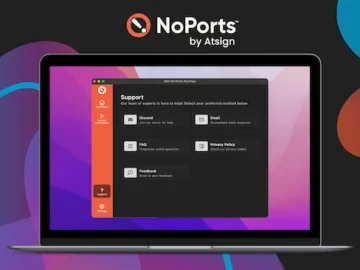
Atsign introduces NoPorts to offer a secure remote access solution, exceeding current limitations and setting a new standard for secure…
The 2022 Medibank data breach / extortion attack perpetrated by the REvil ransomware group started by the attackers leveraging login…
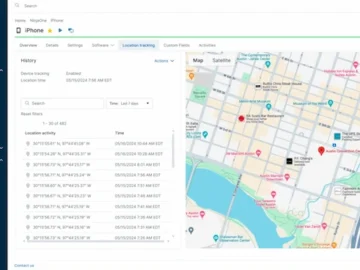
NinjaOne has expanded its platform with mobile device management (MDM). The new solution increases employee productivity and reduces complexity, risk,…
Veritas Technologies announced better choice and flexibility for customers requiring data compliance solutions. Veritas Data Insight, which allows organizations to…