Category: HelpnetSecurity
Action1 researchers found an alarming increase in the total number of vulnerabilities across all enterprise software categories. “With the NVD’s…
Atsign introduces NoPorts to offer a secure remote access solution, exceeding current limitations and setting a new standard for secure…
The 2022 Medibank data breach / extortion attack perpetrated by the REvil ransomware group started by the attackers leveraging login…
NinjaOne has expanded its platform with mobile device management (MDM). The new solution increases employee productivity and reduces complexity, risk,…
Veritas Technologies announced better choice and flexibility for customers requiring data compliance solutions. Veritas Data Insight, which allows organizations to…
VMware by Broadcom has fixed two critical vulnerabilities (CVE-2024-37079, CVE-2024-37080) affecting VMware vCenter Server and products that contain it: vSphere…
Software security requires a creative and disciplined approach. It involves having the vision to develop secure strategy, tactics, and execution….
Datadog launched Datadog App Builder, a low-code development tool that helps teams create self-service applications and integrate them securely into…
Cybersecurity isn’t just about firewalls and antivirus. It’s about understanding how your defenses, people, and processes work together. Just like…
In this Help Net Security interview, Alan DeKok, CEO at NetworkRADIUS, discusses the need for due diligence in selecting and…
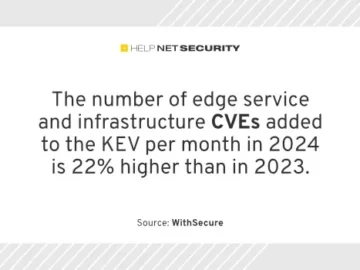
The cyber threat landscape in 2023 and 2024 has been dominated by mass exploitation, according to WithSecure. Edge service KEV…
While 75% of enterprises are implementing AI, 72% report significant data quality issues and an inability to scale data practices,…