Category: HelpnetSecurity
In this Help Net Security interview, Jenn Markey, Advisor to The Entrust Cybersecurity Institute, discusses the increasing adoption of enterprise-wide…
The education system isn’t equipped to handle today’s cyberthreats. I’m not just talking about cybersecurity education in schools shaping the…
Corporate Data Protection Manager GLS | Germany | Hybrid – View job details As a Corporate Data Protection Manager, you…
Security researchers have published a proof-of-concept (PoC) exploit that chains together two vulnerabilities (CVE-2024-4358, CVE-2024-1800) to achieve unauthenticated remote code…
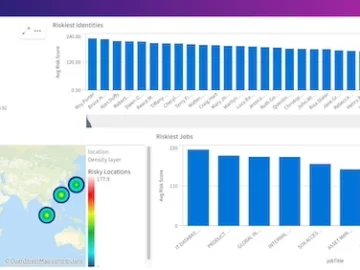
SailPoint has announced a new offering on its Atlas platform, SailPoint Risk Connectors. As part of its Atlas platform, SailPoint…
There’s never been a better time to deepen your skills in cybersecurity as the demand for experienced experts continues to…
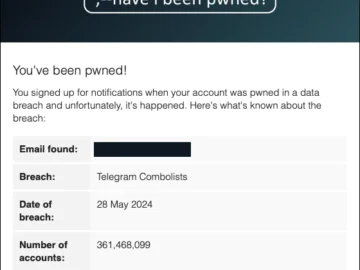
A new trove of 361 million email addresses has been added to Have I Been Pwned? (HIBP), the free online…
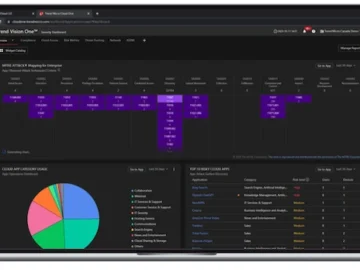
Trend Micro announced its latest breakthrough in network detection and response (NDR) technology: Inline NDR. The technology is available via…
Plainsea is a cutting-edge platform set to shake up the cybersecurity scene with its European launch at Infosecurity Europe in…
Free, open-source cybersecurity tools have become indispensable to protecting individuals, organizations, and critical infrastructure from cyber threats. These tools are…
Modern applications are taking over enterprise portfolios, with apps classed as modern now making up 51% of the total, up…
Zyxel Networks launched USG LITE 60AX–an AX6000 WiFi 6 Security Router designed for small businesses, teleworkers, and managed service providers…