Category: HelpnetSecurity
To secure emerging SaaS attack surfaces, Adaptive Shield has extended the capabilities of its SaaS Security Posture Management (SSPM) unified…
In this Help Net Security interview, Ken Gramley, CEO at Stamus Networks, discusses the primary causes of alert fatigue in…
CISOs have long been spreadsheet aficionados, soaking up metrics and using them as KPIs for security progress. These metrics have…
Although the goals and challenges of IT and security professionals intersect, 72% report security data and IT data are siloed…
Incident response today is too time consuming and manual, leaving organizations vulnerable to damage due to their inability to efficiently…
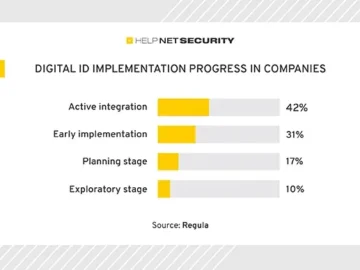
As digital transformation accelerates, understanding how businesses are preparing for and implementing digital ID technologies is crucial for staying ahead…
While fears of cyber attacks continue to rise, CISOs demonstrate increasing confidence in their ability to defend against these threats,…
Chronon is an open-source, end-to-end feature platform designed for machine learning (ML) teams to build, deploy, manage, and monitor data…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Google fixes yet another Chrome…
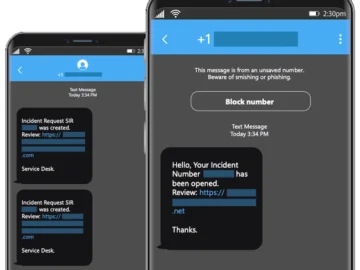
Earlier this month, the FBI published a private industry notification about Storm-0539 (aka Atlas Lion), a Morocco-based cyber criminal group…
One in three organizations are not currently able to proactively identify, assess, and mitigate risk with their GRC program, nor…
For the eighth time this year, Google has released an emergency update for its Chrome browser that fixes a zero-day…