Category: HelpnetSecurity
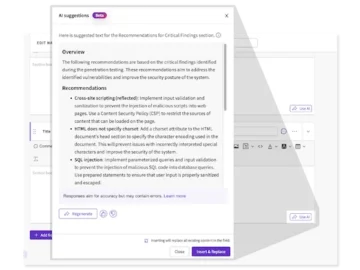
PlexTrac announced Plex AI, the company’s AI-powered offensive security report writing tool, real-time team collaboration to enable simultaneous report editing…
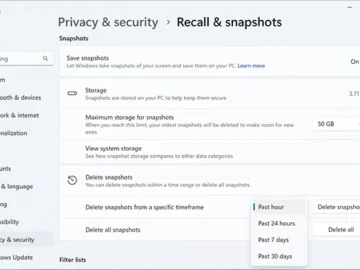
Microsoft has announced the Copilot+ line of Windows 11-powered PCs that, among other things, will have Recall, a feature that…
Veeam has patched four vulnerabilities in Backup Enterprise Manager (VBEM), one of which (CVE-2024-29849) may allow attackers to bypass authentication…
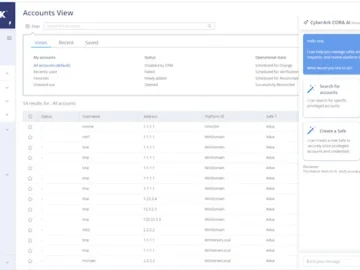
CyberArk announced CyberArk CORA AI, a new set of AI-powered capabilities that will be embedded across its identity security platform….
Associate Director, Cyber Security AstraZeneca | Sweden | On-site – View job details You will develop and implement security policies,…
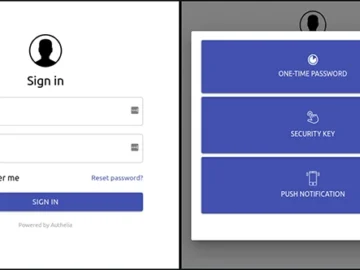
Authelia is an open-source authentication and authorization server that offers 2FA and SSO for applications through a web portal. It…
CEOs are facing workforce, culture and governance challenges as they act quickly to implement and scale generative AI across their…
Security leaders are facing increased technological and organizational complexity, which is creating a new wave of identity risks for their…
Researchers have found 15 vulnerabilities in QNAP’s network attached storage (NAS) devices, and have released a proof-of-concept for one: an…
Tenable researchers have discovered a critical vulnerability (CVE-2024-4323) in Fluent Bit, a logging utility used by major cloud providers and…
Social engineering threats – those which rely on human manipulation – account for most cyberthreats faced by individuals in 2024,…
In this Help Net Security interview, Robert Haist, CISO at TeamViewer, discusses how AI is being leveraged by cybercriminals to…