Category: HelpnetSecurity
The enterprise attack surface is expanding in multiple ways, becoming more numerous and more specific, according to runZero. “Our research…
Here’s a look at the most interesting products from the past week, featuring releases from Calix, FireMon, ManageEngine, and OWASP…
New versions of Git are out, with fixes for five vulnerabilities, the most critical (CVE-2024-32002) of which can be used…
For the third time in the last seven days, Google has fixed a Chrome zero-day vulnerability (CVE-2024-4947) for which an…
Cloud security incidents are alarmingly on the rise, with 61% of organizations reporting breaches within the last year, marking a…
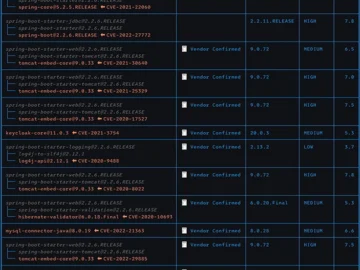
OWASP dep-scan is an open-source security and risk assessment tool that leverages information on vulnerabilities, advisories, and licensing restrictions for…
AI has captured widespread interest and offers numerous benefits. However, its rapid advancement and widespread adoption raise concerns, especially for…
ESET researchers released its deep-dive investigation into one of the most advanced server-side malware campaigns. It is still growing and…
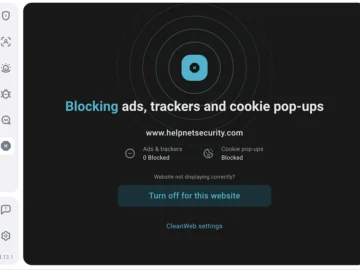
A study by PageFair revealed that ad blocker usage surged by 30% in 2016 alone, reflecting a growing public concern…
Many organizations lack adequate IT staffing to combat cyber threats. A comprehensive approach to cybersecurity requires more than technical solutions….
Threat actors are taking advantage of the flawed design of Foxit PDF Reader’s alerts to deliver malware via booby-trapped PDF…
In this article, you will find excerpts from various reports that offer statistics and insights about the current ransomware landscape….