Category: HelpnetSecurity
On Wednesday, a threat actor named “InteIBroker” put up for sale “access to one of the largest cyber security companies”…
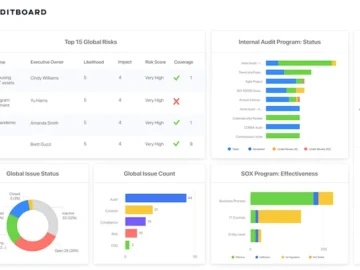
AuditBoard announced powerful enhancements for its InfoSec Solutions to help organizations meet their IT compliance, cyber risk, and vendor risk…
The US Cybersecurity and Infrastructure Agency (CISA) has announced the creation of “Vulnrichment,” a new project that aims to fill…
Cybersecurity is a relatively new challenge for many IoT device makers who have traditionally produced non-connected devices. These devices were…
Ransomware and extortion incidents surged by 67% in 2023, according to NTT Security Holdings’ 2024 Global Threat Intelligence Report. Global…
Recent cyber incidents demonstrate the healthcare industry continues to be a prime target for ransomware hackers, according to Rubrik. New…
In the process of moving to the cloud, you need a security-first cloud migration strategy that considers both your security…
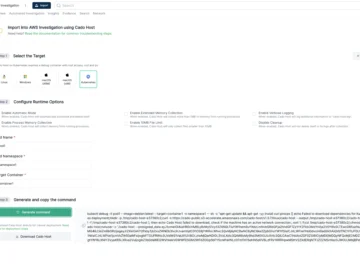
Cado Security has introduced a solution for conducting forensic investigations in distroless container environments. With Cado Security’s new offering, security…
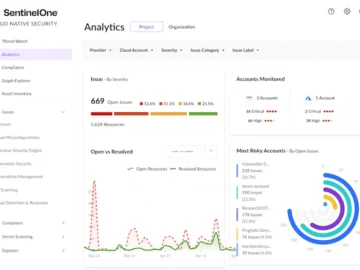
Attackers are targeting the scope and scale of the cloud to run rapid and coordinated threat campaigns. A new approach…
Researchers have brought to light a new attack method – dubbed TunnelVision and uniquely identified as CVE-2024-3661 – that can…
MITRE has shared a timeline of the recent breach if fell victim to and has confirmed that it began earlier…
RSA Conference 2024 is taking place at the Moscone Center in San Francisco. Help Net Security is on-site, and this…