Category: HelpnetSecurity
Adversary Simulation Specialist LyondellBasell | Poland | On-site – View job details The Adversary Simulation Specialist will be responsible for…
63% of organizations worldwide have fully or partially implemented a zero-trust strategy, according to Gartner. For 78% of organizations implementing…
Here’s a look at the most interesting products from the past month, featuring releases from: Akamai, Bitdefender, CyberInt, Fastly, Forcepoint,…
There are proof-of-concept techniques allowing attackers to achieve persistence on Palo Alto Networks firewalls after CVE-2024-3400 has been exploited, the…
The Federal Communications Commission (FCC) fined the nation’s largest wireless carriers for illegally sharing access to customers’ location information without…
Cybersixgill, the global cyber threat intelligence data provider, broke new ground by introducing its Third-Party Intelligence module. The new module…
Security industry leaders believe that AI and automation technologies are critical to addressing the complexities of modern security operations, according…
In this Help Net Security interview, Mike Lemberger, Visa’s SVP, Chief Risk Officer, North America, discusses the severe financial losses…
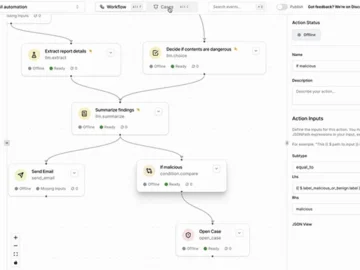
Tracecat is an open-source automation platform for security teams. The developers believe security automation should be accessible to everyone, especially…
Any password under seven characters can be cracked within a matter of hours, according to Hive Systems. The time it…
Organizations worldwide need talented, experienced, and knowledgeable cybersecurity teams who understand the advantages and risks of emerging technologies. Aspiring leaders…
The Product Security and Telecommunications Infrastructure (PSTI) Act has come into effect today, requiring manufacturers of consumer-grade IoT products sold…